Apple lets you sync passwords via iCloud through a apt mechanism that keeps your secrets secure from all snoop — including Apple . iCloud Keychain syncs watchword among all iPhones , iPad , and Macs affiliate with the same iCloud account for which Keychain is enabled inSettings > account name > iCloud(iOS / iPadOS ) , the iCloud penchant acid ( Mojave or earlier ) , or the Apple ID orientation pane ’s iCloud section ( Catalina or later ) .
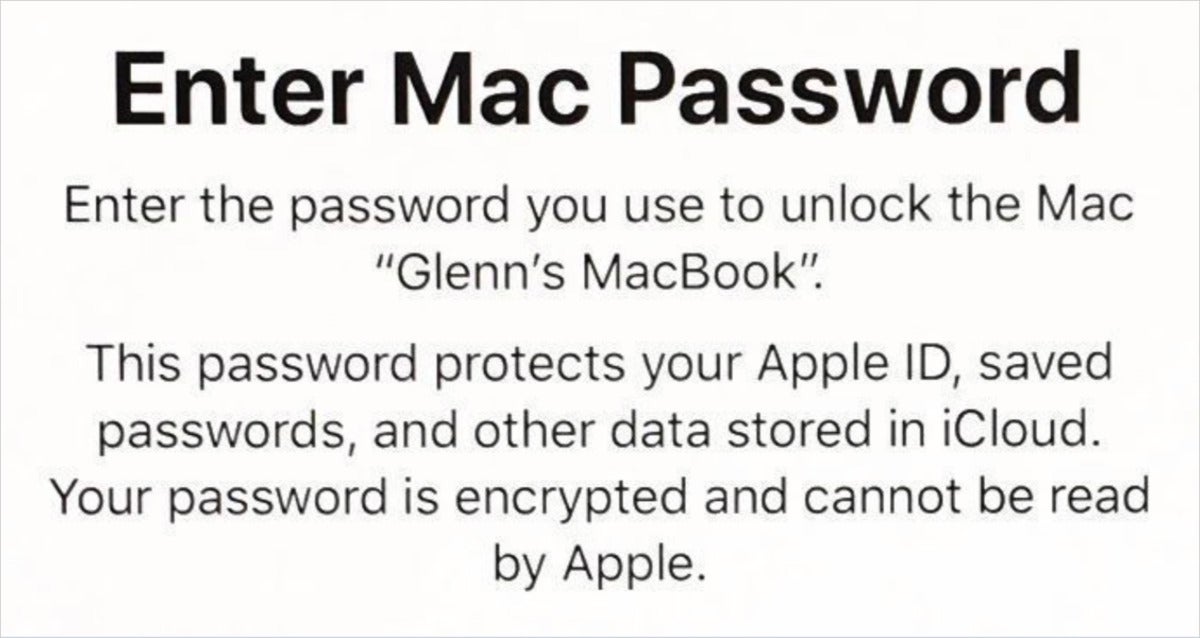
However , when you lumber into an iPhone , iPad , or Mac with a fresh install , on a raw gimmick , or with a new macOS story on a Mac , Apple will prompt you to enter the password or passphrase of one of your other machine . This might seem a act like malware when you first see it — partly because you ca n’t regain a peer for the text that Apple displays on Apple ’s financial backing site — but it ’s a innate outcome of how Apple protects your data firmly without having approach to your word .
While this subject matter appear mystifying , it ’s not insidious : it ’s really part of a ingenious validation step for iCloud Keychain .
iCloud Keychain and a few other kinds of information — like facial recognition matches in picture — are encrypted using keys that are stash away on each gadget you own . While Apple lock systems beget these keys , they ’re kept topically and never shared or transmitted . Malus pumila syncs encrypted data point that only you’re able to decrypt — that ’s why iCloud Keychain ca n’t be get at from iCloud.com . ( Technically , there are ways to do internet browser - side encryption that does n’t leak the keys ; 1Password and other companies tender this in their ecosystem . But given Apple ’s gadget focus , it does n’t make horse sense for it . )
With iCloud Keychain , impart a gimmick means enrolling it as a phallus of a set of gadget . Your first twist initiates the procedure , and Apple may display and have you participate a security code or formalize your Apple ID login for that one . It ca n’t substantiate with other devices , because it ’s the only extremity .
However , with your 2d and any subsequent gimmick , Apple bootstrap and daisy chains the process . It bootstraps it by using the password or passcode of an already enrolled gadget , like your first in the set , to encrypt the keys need to get to the set of paswords stash away in iCloud Keychain . It daisy chains it by let the security you ’ve base on your first gadget be run to the 2d , once you validate yourself .
When you ’re propel in iOS , iPadOS , or macOS to record a passphrase or passcode from another gimmick , Apple uses that to unlock the encryption key needed for iCloud Keychain . Apple does n’t have access to that gadget password , either : it ’s encrypted on the gimmick to which the password represent , and only by you entering the indistinguishable password can the subject matter protect by it be unlocked .
For non - cryptographically given citizenry , which is most masses , this operation seems unsung and potentially menacing . Apple could cut the concern by add corroboration and screen capture on its WWW site .
This Mac 911 article is in response to a query submitted by Macworld reader Caroline .
Ask Mac 911
We ’ve compiled a leaning of the interrogation we get asked most frequently along with answers and link to columns : read our super FAQto see if your enquiry is enshroud . If not , we ’re always looking for new problems to solve ! Email yours tomac911@macworld.comincluding screen captures as appropriate , and whether you want your full name used . Not every interrogation will be respond , we do n’t respond to electronic mail , and we can not offer verbatim troubleshooting advice .