If you have logged in recently with your Apple ID andrequested an SMS - based 2nd - factor verification codeinstead of using the trusted machine method acting , you might have note Apple made a change to the school text you welcome .
antecedently , Apple transport a message like this :
Your Apple ID Code is123456 . Do n’t share it with anyone .
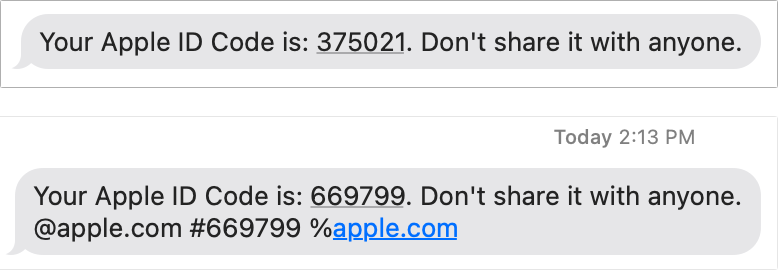
Starting around November 2021 , the codes seem in this format :
Your Apple ID Code is:123456 . Do n’t partake in it with anyone . @apple.com # 123456 % apple.com
Why the change ? Appleproposed in August 2020that it would support“domain - bound codes ” for logins . This sort of code need sites to make a slender addition to the text messages used for confirmation codification . The incoming message has to provide a destination world and some other datum . Apple said that this change would better the integrity of its operating system offering to autofill the codification via a hypnotism in the QuickType saloon in iOS and iPadOS and a fall - down value in macOS Safari and other macOS apps that take advantage of this feature of speech .
Apple offer this variety as a way to deter phishing that tries to intercept and redirect verification codes . In most phishing attacks , the dupe gets directed to a fake site that asks them to enter their credentials . The site takes those credential and silently relays them to login at the legitimate website .
But some attackers are wise to two - divisor authentication . If the site send off a codification via SMS as the nonpayment method , the user being phished receive a school text message with the code . The phisher then prompts for that computer code .
iOS , iPadOS , and macOS offer to fill in the codification most of late come via SMS to the Messages app in any the right way initialize field — including a phishing site ’s verification - code battleground . That makes it too easy on the chiseller .
However , if the text subject matter is scoped as Apple suggested , operating systems starting with iOS 15 , iPadOS 15 , and macOS 11 Big Sur will only offer to autofill on sites that match the knowledge domain name . The security is n’t perfect , but it ’s a simple-minded update to beef up justificative actions .
The format generally look like this :
As a user , there ’s nothing you need to do . The SMS code continue to autofill as expected for valid sites .
However , you may work out increase watchfulness : when you incur a codification in this format as a text message and your app or web browser app does n’t offer to autofill it , you could be open to a phishing lying in wait . Investigate the sphere or app carefully before proceeding .
This Mac 911 clause is in response to a question give in by Macworld lector Kevin .
Ask Mac 911
We ’ve compiled a list of the questions we get ask most often , along with answers and nexus to columns : show our top-notch FAQ to see if your question is covered . If not , we ’re always looking for new problems to puzzle out ! netmail yours tomac911@macworld.com , including covert capture as appropriate and whether you want your full name used . Not every enquiry will be answered , we do n’t reply to email , and we can not provide direct troubleshooting advice .