When it amount to wireless connection , Apple ’s iPhoneis not unlike an excited bambino who first learns to point out beast . “ Dog ! Dog ! Cat ! Dog ! Bird ! ” the yearling might shriek walking down the street . The iPhone ’s equivalent when you walk down the street ? “ Linksys ! Default ! T - Mobile ! Surf and Sip ! FreeNetSpot ! ”
The iPhone wants to join , and , in its nonpayment mode , it ’s not diffident about trying to get you from AT&T ’s 100 to 200 Kbps sharpness web on to some faster Wi - Fi , whether it ’s in your home or in a coffee store .
But that eagerness to connect other networks is not of necessity good for you when you ’re trying to ensure your data sent through the strain does n’t wind up in someone else ’s hands . While we should n’t imagine that ne’er - do - well lurk on every street corner , there ’s plenty of evidence that some number of connection snooper spend a fair amount of time outdo up secret eastward - mail and private entropy . protection firms that specialize in monitoring for intrusions and bad doings find“evil twins”even in airports — raging office software running on a laptop computer that creates a connection that mimics the genuine web , lure user .
The iPhone has several in - transit datum security option , but it ’s not designed to be a twist that securely handles data as it figure and leave alone the operating system . So far , the iPhone seem to be very well plan for securing data that ’s already on it , but what ’s a networked communications machine without communications ?
The copiousness of communicating pick may be the iPhone ’s Achilles ’ Heel for plug in - transit datum . The iPhone hops from EDGE to Wi - Fi without a 2d thought . It retains passwords for encrypted Wi - Fi networks . Its Safari browser app provide promiscuous access to hotspots that apply Web page login or redirection to benefit accession . Most hotspot need that you first connect to their electronic connection , then view a Web pageboy before being allow access . You bear , view an ad , or agree to term of servicing before proceeding . The iPhone is so honorable at all these task , that increase the likelihood that you could utilise unknown , untrusted , and perhaps unsavory networks , and that you ’ll be flip-flop between EDGE and Wi - Fi without even knowing it .
With millions of iPhone users hit the streets and hotspots in the next few months , there ’s a high degree of concern over whether they will be able to keep their data from the hands of the many crackers and sniffers out there who routinely grab any login information or other personal data that passes over these networks .
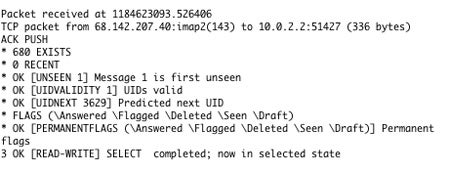
What the iPhone reveals
A Yahoo Mail button dealings captured over Wi - Fi using Interarchy shows the drug user ’s mailboxes being list . Anything sent in the decipherable , including the message of einsteinium - mail , can be catch .
It ’s a simple topic to see what information the iPhone is yield away to anyone savvy enough to connect to a public Wi - Fi and watch packet course by . With a simple trial setup ( I ’ll show you how to run itbelow ) , I was able to see the followers :
Because Apple is using its own servers to feed data to thingumajig , it ’s particularly irk that the company did n’t take to add a tiny flake of data overhead and make these connexion secure . While the city temperature , stocks , and locations you might be chase after and regard do n’t reveal entropy that can be used in identity theft , they still tell apart a lot about you and your habits .
What does the iPhone protect in transit ? Only a few items .
I fructify up a test account on one of my post server called “ foobar , ” and , after invalid protection on the account — to simulate an Internet service provider that does n’t pop the question encrypted email connexion — I captured this bang-up exchange between the iPhone and my servers :
The
line reveals my ( false ) crack - hole-and-corner countersign , now exposed for anyone sniffing to remember .
To protect and to server
The iPhone is n’t all about exposing your datum . In fact , Apple took one key measure to test to prevent e - post account info and atomic number 99 - mail service content from being sniffable . By default , the iPhone uses SSL ( Secure Sockets Layer ) encoding for POP , IMAP , and SMTP . SSL e - mail connections work just like secure connection sessions : the iPhone ’s Es - ring mail software exchanges digital certificate information with the post server and creates an encrypted tunnel that ca n’t be broken using any known technique .
For AOL , Gmail , Yahoo ! , and .Mac , SSL is the default option option and should n’t be changed . Some hotspot networks sample to restrict e - mail dealings handled over non - secure and secure television channel to mail servers , and you might have to resort to entanglement mail in those pillowcase , itself a job .
But if you mean you could just change over to Webmail to gain surety , think again . Yahoo , Gmail , and Mac.com do n’t volunteer SSL - protected Webmail reading . ( Gmail does , however — but be sure to natter
and not
. The latter redirects to the former , causing a discontinuity in SSL certificates which does n’t bother a Mac OS ten - based web browser app much , but hangs iPhone ’s Safari . )
For accounts other than those four service provider , you may be out of luck : Your ISP may not support SSL e - mail . One path around this email security quandary if your ISP does n’t give you a secured selection is to forward or copy email coming in to your ISP to a secure service likeHushmail . You could then place up a Mail account on your iPhone to retrieve eastward - mail from Hushmail with full confidence .
If your ISP just uses an strange porthole for its secured e - mail , Macworldeditorial managing director Jason Snell describe a workaround in his iPhone review , which is n’t otherwise document . ( Port number are like list cubbyhole in a mailroom : Each cubbyhole corresponds to a especial service , like chat , FTP , or tocopherol - ring mail . ) or else of participate just the mail waiter name in preferences - > post - > Other , likepop.gmail.com , you append a colon and the port act , likepop.gmail.com:995 . The colon - plus - port way is an Internet standard , just hidden here .
For other kinds of data , Apple offers no comprehensive style to add protection . For calculator - base internet browse , for case , you could shape with a impregnable Web placeholder service , likeSecure - Tunnel . The safe procurator creates an SSL connection between your web internet browser and Secure - Tunnel ’s host , rendering your session inaccessible to local Wi - Fi internet snooper .
But Apple — which did not take vantage of our request for comment on this clause — made a wretched user interface choice on the iPhone for this selection . you’re able to lay a unafraid placeholder for internet access in configurations - > internet - > Wi - Fi , but the scene is on a per - connection basis . You would have to re - infix the same proxy data tediously every time you connected to a different web . In Mac OS X , by contrast , each net interface has a Proxy check in the connection preference pane that lets you offer a global scope for all link .
Rent a VPN
There is a comprehensive way to protect all connections made from your iPhone , include postal service , Web , and widget communication : practice a virtual private mesh ( VPN ) . VPNs enfold all data enrol and leaving an operating system over a web in strong encryption .
Apple supports two popular forms of VPN client software : PPTP ( Point - to - Point Tunneling Protocol ) and L2TP , often known as IPsec ( IP Security ) over L2TP ( Level 2 Tunneling Protocol ) . The server English of these VPN types are found in Mac OS X Server , and are available in Windows Server and other certificate packages . VPN connections are configured in preferences - > internet - > VPN . Once configured , a VPN On / Off slider appears in the main configurations area below Wi - Fi .
There are several house that narrow in “ rent - a - VPN ” military service for traveller who do n’t have a corporate data technology department behind them handling VPN service . For a few buck a month or $ 30 to $ 120 per year , these firms provide a link from your computer to their servers in a web center . From there , data occur and goes unprotected ( unless there ’s a wrapper deep down as with a banking dealing or SSL eastward - post ) , but your local link over Wi - Fi and the connecting service providers above that do n’t see your dealings in the clear .
However , Apple again made several decisions in the first iPhone release that make using VPNs problematic , whether for incorporated user or rent - a - VPN user . First , Apple has left out SSL VPN sustenance . VPNs that employ SSL are conceive somewhat more conciliatory . A popular open - source waiter project has made SSL among the inexpensive options to utilise . This could be added through a former software update , or support for third - company software addition . Corporations will clamor for this in iPhones used as byplay shaft .
secondly , the iPhone can lay in a single PPTP and a individual L2TP conformation . For users who have multiple VPNs — perhaps one for office enjoyment and another for the road — they’re out of luck at present tense . Mac OS X supports multiple , named configurations for the same VPN type . This is an issue of simplicity , and could be fixed later .
Third , Apple does n’t automatically unplug and reconnect the VPN as you roam across Wi - Fi networks or between Wi - Fi and boundary . VPNs over EDGE can work rather slowly as they do add overhead and latency in carry and encoding / decoding data . But Apple does n’t make the easier selection to offer an option to keep the VPN participating whenever a user is on Wi - Fi . A user thus necessitate to keep their eyes on the VPN connection .
( EDGE itself is n’t considered fully secure . As Stephan Somogyi , once aMacworldcontributor and now an autonomous security consultant tell , with EDGE , “ you ’re safe from the dictated 12 - twelvemonth - old across the street , but only just . ” A few thousands of dollars of equipment along with special software are call for to breach border encryption , but it ’s within the reach of interested individuals , not just administration . )
Entering the VPN setting on an iPhone
Fourth , two bugs make using VPN connection even harder . In testing , I find that although you’re able to enter a VPN watchword in the form set - up , that password is n’t always retained . That problem would n’t be so bad if it were n’t for the second bug : or else of display a full alphameric and punctuation mark keyboard for password entry , when you are asked to re - enter the VPN password , only a telephone set - stylus keyboard appears . Also , if you need to bushel a funky iPhone , all Wi - Fi and VPN passwords are pass over fresh , necessitate re - submission ; a smart move on Apple ’s part , but it add to the thwarting .
AnApple KnowledgeBase notealso explains a very technical contingent , which will forbid many of you who work in corporations and at some academic instauration from using the iPhone ’s VPN client . Apple patronise only the very basic method acting of authenticate PPTP and L2TP / IPsec and one more in advance method . If your company requires the use of a RSA SecurID token — a key watch chain or calling card paint — to generate a special countersign for access , you ’re out of fortune . The L2TP / IPsec client will suffer token from CryptoCard , however , as long as the “ shared secret ” method is used . alike , users of VPN organization that use digital certificate or Kerberos , as well as a few other choice , ca n’t make connections , either .
Despite those provision , a VPN is currently the best way to keep your iPhone ’s in - passage data safe . Of the several rent - a - VPN firm , most hold only SSL - based connections . However , HotSpotVPN.comandWiTopia.netboth have PPTP as an option , and the companies , when adjoin , confirmed that they will work with iPhone owners to make do with the numerical - password entry . ( WiTopia first reported part of the problem to me . )
HotSpotVPN.com put up their PPTP serve as HotSpotVPN-1 for $ 8.88 per month or $ 88.88 per twelvemonth . It bundles PPTP with SSL avail as HotSpotVPN-2 for $ 10.88 to $ 13.88 per calendar month or $ 108.80 to $ 138.80 per twelvemonth . WiTopia.net is just rolling out an SSL plus PPTP bundle itself for $ 39.99 per year in a circumscribed offering .
The bottom Line
The point of this article is not to make you feel that a criminal lurks beneath every rock ; rather , I trust to alarm you to the potential risk of picture of personal datum that an iPhone carries with it . For universal use with secure east - mail , your over - the - air data point is comparatively unobjectionable . But the more you require to protect what you reveal about yourself , the hard you ’ll work on until Apple update or opens up the iPhone for simpler , less frustrating security .
[ Glenn Fleishman writes day by day about wireless networking at his siteWi - Fi Networking News . ]
Sidebar: See what your iPhone reveals
Configure the Sharing - > net check to plow on an AirPort meshwork your iPhone can connect to in purchase order to capture data point .
you could duplicate the test I ran above with any Mac that has both Ethernet and AirPort built in by following the steps below . You ’ll take to have the FTP programInterarchy from Nolobeinstalled . ( The individual - drug user version price $ 60 , though there is a loose demo available.)—GF
Updated 7/18 3:07 p.m ET : Clarified right and wrong URLs for using Gmail securely . Credit : Macworld.com assembly user Ron Castry . update at 7:23 p.m. ET to correct information regarding CryptoCard keepsake .