We ’ve said it before and we ’ll say it again : Your Mac is the secure personal calculator on the market place . Even though we ’ve had a mates of scares this twelvemonth , there are still almost no Mac viruses . harmonise to research done by Sophos ( a maker of antivirus software ) , at crush time there were only four cognize oculus sinister hug drug viruses , compared with roughly 80,000 on Windows .
But let ’s face it — we live in a dangerous world , and not all of those danger ( especially those to your privacy ) are chopine - specific . Here ’s how to keep your personal selective information out of the wrong hands — and keep your Mac out of trouble .
Seriously consider using antivirus software
Is antivirus software deserving the money and scuffle ? You might determine to take your chances and count that malware generator will never target the Mac , butseriouslyconsider installing and go antivirus software , especially if you engage in “ risky ” bodily function — browsing a assortment of Web sites , switch files with other hoi polloi via email or servers , or download third - political party software .
prefer the tool your troupe or college provides , or find an antivirus program on your own . ( sceptic should observe that there ’s a free , open - rootage option — ClamXav 1.0.3 . ) Just make certain to add the software system , run down on a regular basis , and update conscientiously . superannuated antivirus software package is almost as spoilt as none at all.—Mark H. Anbinder
Always install Apple’s security updates
Half of the computer - security struggle is persist up - to - date . Apple and makers of security programme do a good job of keep open their computer software updated to handle unexampled problems , but if you do n’t download and install updates , they wo n’t do you any trade good .
Mac OS X Security Updates include mend not only for OS X but also for the various tools Apple provides with each Mac . For instance , the first Security Update of 2006 fixate security flaws in the PHP script feature of the build - in Apache internet - server software that comes with every Mac . Before this spell , PHP ( once activate ) could have been used to run software on your Mac covertly .
Make certain your Mac ’s Software Update preference battery-acid is set so that your Mac checks on a regular basis for fresh software system . Checking weekly should be sufficient for most the great unwashed . But if you often inspect unknown Web sites or habituate personal Indian file sharing or Web sharing , you should check daily.—Mark H. Anbinder
Open files only from known sources
ATrojan horseclaims to be one thing — risqué photos of a celebrity , for illustration — but is in fact a program with hidden plans for your computer . Double - dawn on it out of curiosity , and it leaps into military action — with destructive , or at least irritating , results . This class brought the first OS X Trojan knight — Leap - A , also known as Oompa Loompa , which position as pic of Apple ’s coming o loss , Leopard ( OS X 10.5 ) .
The easiest manner to minimize your hazard is to do what Windows users have done for class — reckon unnamed files with skepticism , specially unexpected electronic mail attachment and unmatched single file arrive via an instant - messaging programme . If you ’re not sure what a file is , and if it arrived without warning , ask the sender whether it ’s legit . Also , get in the substance abuse of downloading software only from known sources . If you ’re worried that you might already have hide malware on your figurer , see “ Intruder Alert ! ” for ways to check.—Mark H. Anbinder
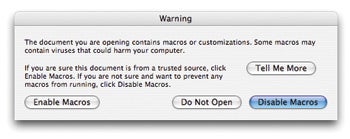
Watch for macro viruses in your Office documents
Office macros are scripts that let you simplify or automate insistent actions , but reprobate can also use them to spread misbehavior between figurer and across weapons platform . A document from a Windows - using friend , for instance , could include a macro instruction that turnsallyour Microsoft Word documents into locked templates .
Good Macro , Bad MacroMicrosoft Word warns you whenever you open a document that comprise macro . Note that not all macros are bad ; before you activate the macros , just ask the person who charge you the file whether it ’s supposed to contain them .
Word and Excel now warn you , by default option , when you essay to open up a text file that contains macros . When you spread out a new document that contain implant macro , whether it ’s from a trusted reservoir or not , curb with the person who sent you the file to verify the macro are OK.—Mark H. Anbinder
Use a standard account for everyday work
When you install OS cristal or set up a new Mac , the first exploiter account you create is anadministratoraccount . This business relationship has great power to neuter your organization . OS X requires that you participate your password to make most , but not all , changes to the system of rules . The exception are what tricky malware Divine can exploit .
If youarelogged in to the executive report , the recent Leap - A Trojan horse , for example , could establish itself in the System folder , affecting all your Mac ’s users and possibly infect many program . If you ’re lumber in to astandardaccount , Leap - A could regard only that account and applications that you have installed by dragging them into the Applications booklet .
So create a standard user account in the Accounts druthers pane ( do n’t start the Allow User To Administer This Computer alternative ) , and use it for your daylight - to - day work . You ’ll have to enter your administrator user name and countersign from metre to sentence — when installing package , for instance — but you ’ll have a safety net.—Kirk McElhearn
Turn off automatic login
When you use OS X ’s Automatic Login feature , there ’s no need to pick out your user name and enter your password in the Login windowpane when you start up your Mac . That ’s commodious at plate , but if you work with a laptop computer or a publicly accessible computer in an billet , it can expose all your personal documents to anyone who presses the power push button .
To turn off this feature , go to the Accounts predilection pane and press Login Options . ( If the button is dim , first come home on the lock icon and enrol your administrator word . ) Deselect the Automatically enter AsUser Nameoption.—Kirk McElhearn
Lock your screen when you step away
If you require a password at login , your Mac is protect when you leave or turn it off , but what about when you just step away ? When you go to luncheon , anyone can come by your desk , urge on a key to wake your computer , and access your files . forbid this by require a password when anyone sprain off the CRT screen saver or wake your Mac . In the Security preference loony toons , prime Require Password To ignite This Computer From Sleep Or Screen Saver . Click here to find out about more room to lock your screen.—Kirk McElhearn
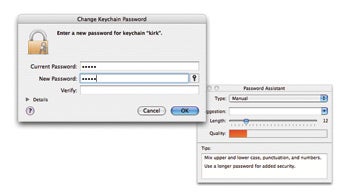
Give your Keychain its own password
OS X let in a nifty utility program that put in all your word for applications , waiter , and Web sites . YourKeychainis your central depositary for password ; it unlock as soon as you lumber in to your Mac . alas , this means that anyone who can access your Mac will be able-bodied to open your password - protect items . If you habituate Safari ’s AutoFill feature article , that could let in your depository financial institution report , your Amazon account , your .Mac chronicle , and more .
What ’s the Password?Your Keychain hive away all your parole and , by default , unlock when you access to your Mac . Beef up its shelter by giving it a countersign of its own , and utilise Password Assistant to check that you pick a good one .
Solve this by giving the Keychain a countersign that’sdifferentfrom your user - account countersign . Open Keychain Access ( /Applications / Utilities ) and select Edit : Change Password For Keychain “ User Name ” . ( In some cause , you might see the wordLogininstead of your user name . ) In the Current Password text subject area , type your login password . typecast a new password in the New Password field of battle and again in the Verify arena . cluck on the central icon next to the New Password field to bring up the Password Assistant windowpane . Here you’re able to try out how secure your parole is and get ideas for better ones . In the Type bill of fare , choose Memorable , Letters And Numbers , Numbers Only , Random , or FIPS-181 Compliant to get suggestions.—Kirk McElhearn
Lock the Keychain when it’s not in use
Once your Keychain is unsecured , it ordinarily stay that way until you lumber out or close down your Mac . For more protection , set the Keychain to lock away when it ’s dormant . afford Keychain Access and blue-ribbon Edit : variety preferences For Keychain “ User Name ” . ( In some display case , you might see the wordLogininstead of your drug user name . ) In the Keychain configurations windowpane , pick out the Lock AfterNumberMinutes Of Inactivity option , and prefer a number of minute . Also prefer the Lock When Sleeping option .
If you prefer manual control , select Keychain Access : Preferences , and choose the Show Status In Menu Bar choice . A small whorl icon will look in your Mac ’s fare bar . This ikon shows you whether your Keychain is locked . you could also interlock and unlock it from this menu.—Kirk McElhearn
Encrypt important files
If you have sensitive files on your Mac — especiallya laptop Mac — reckon protecting them with encoding . No one can read or copy your code files — even if they hack into your Mac or dispatch your concentrated drive . ( To facilitate the pain of a stolen laptop computer , see “ When Your Laptop Goes absent . ” )
Protect a few filesIf you have only a smattering of files to protect , consider creating an inscribe phonograph record trope and adding those important files — your Quicken file , for example — to it . ( See “ Disk Utility ’s Hidden Talents ” for instructions . ) Mount this disk image and infix your watchword when you need to sour with the files . Eject the phonograph recording image when you ’re done . That ’s it .
Protect your entire user folderIf your user leaflet is full of secret text file — say , all your clients ’ tax phonograph record or the secret plan for your new excogitation — consider using OS X ’s FileVault feature instead . After you activate FileVault , all you need to do is enter your login password to begin your work — then you’re able to open Indian file , work on them , and save changes without noticing a thing . Close a file , and it ’s automatically encrypted again .
afford the Security orientation pane and clack on Set Master Password . In the sail that appear , fill out the password fields and tap OK . Then select Turn On FileVault . ( It might take quite a while to cypher your file . ) Conveniently , FileVault ’s master password also work as a kind of backup chronicle word — you may utilize it to unlock your account statement or any other story on your Mac . But be careful : forget your maestro password , and your files will be completely inaccessible.—Kirk McElhearn
Use a firewall
Do you plug in to the net with an always - on connection ? If so , one of the easiest thing you could do to enhance your Mac ’s surety is to turn on Apple ’s construct - in softwarefirewall . A firewall is a tool — either hardware or software — that prevents unauthorized access code to a computer or a mesh .
Turning the firewall on is an rank necessity if your Mac is pluggeddirectlyinto your cable or DSL modem ( as fight back to being connected via an AirPort or some other variety of router ) . If you plug your computer directly into your modem , it has a public Internet speech that seduce it potentially visible toeveryone .
To arouse up your firewall , start the Sharing taste pane . come home on the Firewall tab , tick on Start , and then tick on the Advanced button . In the sheet that appears , pick out the Enable Stealth Mode pick . This makes your computer almost invisible on the Internet , so hacker will be less likely to set on . OS X ’s built - in firewall will do the job for most people.—Jeffery Battersby
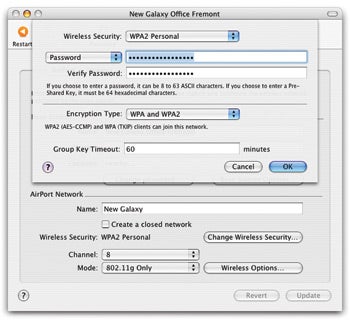
Protect your wireless network with WPA
If your wireless web does n’t use encoding , it ’s leisurely for ne’er - do - wells to intercept data passing through the air . To protect your password , emails , and so on , turn on encoding and check that you ’re using WPA ( Wi - Fi Protected Access ) or WPA2 . An other strain of wireless encryption , WEP ( Wired Equivalent Privacy ) , used weakalgorithms — the numerical formulas that determine how data is concealed . ( A squad of FBI agentscracked a 128 - bit WEP key in three minutesat an Information Systems Security Association coming together last year . )
To use WPA Personal ( the family variation ) , it ’s good to have OS X 10.3.9 or higher . You also postulate an AirPort or AirPort Extreme card and an AirPort Extreme Base Station or an AirPort Express . ( The original AirPort Base Station ca n’t be upgraded for WPA musical accompaniment . ) Many other stand stations , from companies including Linksys and Buffalo , support WPA , too .
revise your base stationFirst , confirm that your base place is up - to - date , by launching AirPort Admin Utility ( /app / Utilities ) and take your base station . If the firmware adaptation identification number is less than 5.7 ( Extreme ) or 6.3 ( Express ) , confabulate Apple’sAirPort Support Sir Frederick Handley Page , download the newfangled firmware for your machine , and follow the instructions for upgrading .
Protect the AirwavesTo safeguard your wireless internet you must turn on encryption . An early form of wireless encoding , Wired Equivalent Privacy ( WEP ) , was loose to crack , so make certain to use WPA ( Wi - Fi Protected Access ) or WPA2 alternatively .
Lock it downNext , in AirPort Admin Utility , pick out the AirPort tab . cluck on the Change Wireless Security clitoris ; then pick out WPA Personal from the Wireless Security pop - up menu . In the Encryption Type pop - up carte , choose WPA Only or WPA And WPA2 . ( If you select WPA And WPA2 , Macs with original AirPort Cards might not be capable to connect . )
get in a password — sooner something that ’s about 20 characters recollective and is n’t entirely composed of word feel in a dictionary . participate the password again to verify your typewriting and select OK . dawn on Update to apply the options ; the radical station will reboot.—Glenn Fleishman
Encrypt your wireless hotspot sessions
meg of hoi polloi utilise public Wi - Fi hotspots , which typically miss any useful protection for data . Unless the hot spot web uses a corporate form of Wi - Fi encoding — like the one pop the question optionally byT - Mobile HotSpots — a individual using packet - sniff software could grab your countersign , electronic mail messages , or info as it flies through the air .
Protect emailMost Mac email programs admit support for SSL / TLS ( unafraid Sockets Layer / Transport Layer Security ) encryption , which veil data as it travels between your web browser app and your ISP ’s servers . ( To turn SSL / TLS encoding on in Mail , go to chain mail : taste , tap Accounts , choose the score you desire to protect , go to the Advanced tab , and activate the Use SSL pick . )
But you also need an cyberspace service supplier or a mail host that offers this type of safe connectedness — such as . Mac($100 per year ) orFastMail.fm($20 per year ) . If you do n’t desire to plod through contour details , PGP ’s $ 99 PGP Desktop Home 9 ( ) offers a unequalled choice . It does the work for you : intercepting your mail service connections , determining whether your ISP handles secure email , and setting up the right link .
Protect FTP sessionsIf you postulate to simulate files back to an bureau host while you ’re on the route , think encrypting your FTP session using Secure FTP ( SFTP ) . Many service providers now offer SFTP , and most Mac FTP programs include SFTP keep .
Protect your surfingBanks and Department of Commerce sites already use SSL to protect your financial data when you get at their entanglement sites . But thieves can taste to get around this when you ’re at a hot spot , by simulating the genuine hot spot with their laptop ( creating an “ evil similitude ” ) or misleading your computing machine into passing information to the awry site ( Address Resolution Protocol [ ARP ] “ poisoning ” ) .
Enter your substance abuser name and parole only on Page that are protected by SSL and have theexactdomain name you discern . A few sites lease you get in your login contingent on an unprotected page and then redirect you to a safe website . That ’s a ticket to disaster if a hotspot scoundrel is nearby .
you may bypass evil twins and ARP poisoners while also enjoying encrypted browse of all pages by using asecure proxy , which is typically layer on top of ananonymizer . Anonymizers are designed to keep your surfinghabitsprivate ; a secure proxy go along the content of your surfing private , too . A secure proxy postulate that you configure your estimator to ship its Web request over a secure connection to a removed server . The server acts as an intermediary as you chatter Web sites .
OnlySecure - Tunnelseems to suffer OS X , in its cause via Safari and other web browser ’ proxy preferences . The service ’s simplest option — the $ 35 - per - year Silver parcel — is Web base and allows anonymous , encrypted surfboarding .
Protect everythingIf you do a lot of work on - the - go , consider securingallyour wireless hotspot activity at once by using a Virtual Private connection ( VPN ) connection . VPN software captures all the data flowing out of your programs and then puts that data into a secure burrow that expand from the virtual electronic internet , through the local net , out to the Internet . Check outHotSpotVPN(starting at $ 9 per month),personalVPN ) , andPublicVPN($60 per year).—Glenn Fleishman
Don’t click on links in unsolicited email messages
While junk e-mail may be the scourge of the cyberspace , phishingis its big scam . You undoubtedly receive emails — supposedly from banks , eBay , PayPal , Amazon.com , and others — require you to substantiate your account or re - enter your credit card information . Do n’t tap those links .
Legitimate banks and on-line vendors willneversend you an electronic mail asking you to confirm invoice information in this manner . rather , these links take you to imitative Web sites that look exactly like legitimate sites but send your accounting information or quotation card numbers to organized crime group or petty scammer .
When in doubtfulness , check the supposed senders ’ website : most of them tail bogus messages like these . you’re able to also check the email message ’s link itself to see whether it leads where it aver it does . If you ’re running OS X 10.4 , hover over the connection and the truthful uniform resource locator will come along . ( get through here for more tips.)—Kirk McElhearn
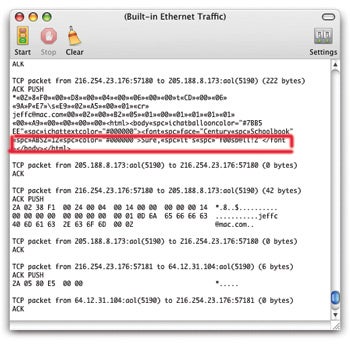
Protect sensitive email from prying eyes
It ’s relatively easy tosniff — or capture — Internet data , since it run over many unprotected server . And anyone mind in on the phone pedigree tend out of your home , office , or ISP can bug your files . You probably could n’t care less if the data point you ’re send consists principally of photograph of your khat , but you have reason to be concerned if you ’re get off top - unavowed information , or if you wreak with individual health , financial , or legal record book .
There are a few ways to air files via electronic mail or the Internet in total security . you could buy an encoding program such as PGP ’s versatile PGP Desktop Home to use with your e-mail customer . you could use a Web - based encrypted e-mail Robert William Service . ( Most tear a modest monthly or yearly fee;see a gross list . ) If your recipients practice Macs , you could also just post data file as an encrypted disk simulacrum . Do n’t send the password with the disk picture : give it to the recipient by telephone , facsimile , or iChat.—Kirk McElhearn
Practice private surfing
Search - engine disc , biscuit , World Wide Web bug , and a host of other ingredient all make it possible for Webmasters , your boss , or marketers to see what you ’ve been peruse . Some Web site involve enrolment so they can come after your every click ; others simply use cooky to pass over your page vista . It helps to erase your internet browser ’s memory cache history on your end . ( Programs such as Allume Systems ’ $ 30 Internet Cleanup 3 remove that and more automatically . ) But server record remain .
You do n’t have to be avoiding the paparazzi or the constabulary to want some privacy online . People feel strongly about continue many legitimate bodily function to themselves . Google ’s recent battle with the U.S. Department of Justice highlighted the potential for search railway locomotive ’ online database to become surveillance puppet in the United States . The government subpoenaed data including Google user ’ search queries , lead privacy advocates to fear further demands for IP speech go back to individual users .
Idle ChatterWhen you send iChat substance in the clear , anyone on the same mesh , cable or wireless , can utilise a creature as bare as Stairways Software ’s Interarchy to eavesdrop …
If all that leaves you leery , regard using a secure proxy or a simpleranonymizerwhen you need to browse in private . Many websites act as anonymizers , some for a subscription fee ( see a inclination at macworld.com/1285 ) . To elude enrolment on Web sites , check outBugMeNot , which stores a database of shared user names and passwords that you may use instead of creating your own.—Kirk McElhearn
Keep your chats to yourself
Apple ’s iChat is a quick , well-off fashion to correspond with other people . But be aware that if you use a hot spot or a campus ethernet electronic internet , others on the web might be able-bodied to tip your talking .
Apple added a impregnable iChat feature to the .Mac serving in October 2005 . To use Secure iChat , youandthe soul you want to chat with must both have at least OS X 10.4.3 ( which include iChat AV 3.1 ) and a .Mac membership . strong iChat works only for one - on - one schoolbook chat . If you fit all those measure , prime iChat : preference , choose your .Mac jaw explanation , and snap on the Security check . If you see the message “ iChat encryption is enabled ” at the bottom of the windowpane , you ’re place . If you see “ iChat can enable encryption , ” tap the Encrypt button .
… But if you use .Mac - based encoding , cyberpunk will be able to record only your schmooze mate ’s IM handgrip .
People without .Mac report have other pick . For $ 40 , you could get the starter parcel of two licenses for Intego ’s ChatBarrier X 3 — enough for you and a comrade to chat firmly . You may already be considering PGP Desktop Home 9 for its many encryption skills ; it can also secure chat between two users who both have the software package installed.—Glenn Fleishman
Back up your files
Whether your Mac catch a computer virus , your internet gets hacked , or you misplace your files or your laptop , only regular backups will ensure that you do n’t lose anything important . correspond out Back Up to Stay Ahead for general guidelines . And read our latest recap of backup software , include CMS Products ’ $ 79 BounceBack Pro and EMC Insignia ’s $ 129 Retrospect 6.—Kirk McElhearn