I hate to pound holes in adept - faith exertion to improve the integrity and security measure of mortal ’ and patronage ’ data point , but in just the last week , I ’ve go through three freestanding efforts that each attempt to pay off a problem , but only figure out a top layer . The underlie blemish continue , and they ’re not at all the fault of those party .
However , the route to hell is built on skillful intention , and the best path to get off that main road is to examine all efforts with a steely glint .
No, look over there
In April , Google liberate thePassword Alert extensionfor its Chrome web web browser . Theextension captures and transforms your passwordwhen you lumber in to any Google site , put in it in a non - recoverable formatting against which other password entries may be checked . ( Seeits FAQfor storage item . )
Then , whenever you utilise your web browser to enter that password at any non - Google site , the extension service warns youthat you ’ve been phished , and recommend immediately changing your password for the Google account . This requires that you practice a unique password for any Google account . Otherwise , you ’ll see this warning on any site into which you put forward a login with the same password .
Google ’s Chrome telephone extension warns you after you ’ve submitted a watchword that ’s also used for a Google - running site .
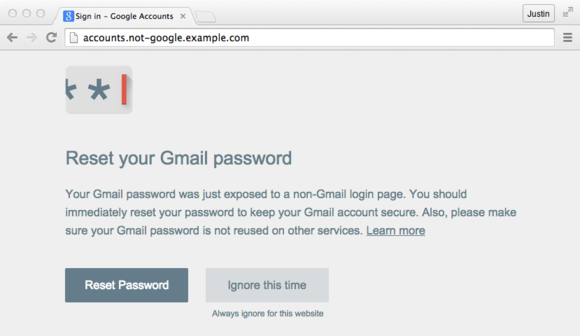
It ’s a clever theme , although it has the cow’s - out - of - the - b problem of warn you post entry rather than aver , “ Whoa — you’re sure you want to give in this ? ” ( It would require rather more watchfulness and C.P.U. cycles to do that . )
But it ’s sham security . While it can aid both naive and advanced drug user , even the savviest arefooledwhen they’represented with phishing pages(PDF ) that are expertly made to resemble licit web site . Researchers quickly found workarounds — many workarounds — to Password Alert . Some bypasses may be inconceivable to prevent , thus ply a subtle false positive signal to users that everything ’s ok .
A word of advice is better than none , but false security measure can lull people into letting their guard down , too . Google will continue to amend the denotation , but they may be unable to make it robust enough to swear upon .
Security through assurances?
I received a flurry of e-mail last week aboutSoverin , a new email service that was become to be radical around client information and secrecy .
What ’s unlike ? Nothing technical . They ’ve founded their enterprise in resistance to Gmail , more or less , pledge through contract and privacy agreements to keep back and use as small of its customer ’ personal information as possible , and definitely not examine to deal details ( even in conglomeration ) to marketer or display advertising . It ’s a paid service at a temperate price .
While theirprivacy policyis exhaustive and welcome , they ’re using standard encrypted IMAP service for retrieve email . This is effective in protect data in transit if implemented well , but mail residing on its servers will be available to anyone at the company and any law - enforcement agents or snapper who acquire entree . ( They encrypt email backups with a unique user code , which is saucy , but email in IMAP storage has to be unencrypted . )
The house is ground in the Netherlands and has located its server there , too , so Soverin is taking advantage of more tight Pentateuch found in Europe related to data point privacy than are present in almost any other part of the mankind . Still , I ’ve been take toFastmailfor many year , and the difference between the pay Fastmail service and Soverin looks like a marketing glide slope free-base on server geographics .
Remind me again of that code?
The folks atMacPawmake a variety of useful utilities , including disk degunkers that find and take unneeded files and extra , some of which may feign organisation public presentation in the right circumstances . ( It ’s more rare that a file cabinet slow down your computer down , and more likely that a private road that ’s approach full reduces performance as OS X moves section of files around and writes temporary or swap files to disk . )
But I have mixed feelings about its just - released , free , OS X / Windows transverse - platform compatibility file cabinet - encoding software , Encrypto . There ’s nothing wrong with the plan of attack , the interface , compatibility , or its simpleness . Rather that it ’s taste to solve the wrong job in the right way .
The software system lets you pluck a password of any complexness and then also offer a clue that can be publicly consider by anyone with the Encrypto computer software on either program . The hint is supposed to provide a jog to memory that a recipient can practice to decipher a file cabinet .
There is a dearth of dim-witted , powerful file - encoding software , so I want to like Encrypto . But the hint part is extremely knotty . Providing a hint , however obscure , boil down the universe of likely passwords , because the hint has to be a clue that a recipient can transmute into something meaningful .
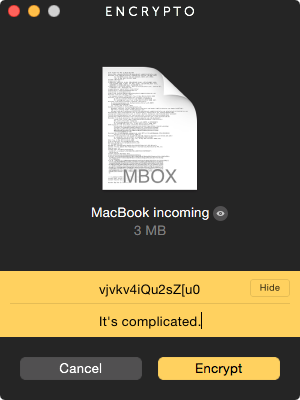
Encrypto lets you coiffe a strong password and then a speck that ’s shown to the recipient role to even up their memory .
I can ensure you that if my hint to an old protagonist is “ that terrible joke about Hellenic clothing ” they would follow up with “ Euripdes , Eumenides . ” But so , too , would many others — it ’s an erstwhile , old gag — and it would supply the cue for a modest universe of combinations of words to be tried , should another political party get ahold of the file .
If the file is n’t important enough to vex about a malicious third - party hacking into it , then why use encryption ? If it is , then why use a method that ’s warrant to have a highly exposed flack airfoil ?
This problem has been solved in many way by many company , but it almost always imply an ecosystem . Kudos to MacPaw for trying to avoid having a public - cay or other encryption base as a essential . It ’s dead simple , and I love that .
But they need to cipher out a method acting to allow multitude to use strong passwords that are associated with simple hints that no third party could ever associate — like a code book , in which a word likemaryjanemeant to use passwordvjvkv4iQu2sZ[u0 . birth a local component that allowed two parties to generate a computer code list that would be encrypted and stored local , and could be partake in some very careful way would offer the expert of both worlds .
Even a deal secret used for the purposes of increasing entropy — making it vastly hard to employ brute force to find a password match — would release this nifty musical theme into something that truly improved security .
Right direction, wrong approach
For users to achieve an goal to fear of routine or unimpeded interception , the putz provided have to be strong enough by default — no additional management should be required . That ’s why iMessage has done so well : the end - to - conclusion encoding is strong and effortless . But iMessage is n’t appropriate for all kinds of data point transmission , and some masses would favour not to rely on Apple ’s technology and assurances .
This is all the right direction , but more pragmatism about what ’s truly being offer and how it ’s being key is demand as well .