On Tuesday , researchers from Skycure disclosed at the RSA conference that a previously known iOS flaw related to automatic Wi - Fi internet connection and a newly get a line SSL certificate handling error could get an iPhone or iPad to ram andendlessly rebootas long as it remains within scope of the electronic internet . ( Skycure sells monitoring and palliation systems . )
The trouble of devices mechanically join Wi - Fi networks is longstanding , and the researchers highlighted a specific aspect of it that they first expose in 2013 and labeled itWiFiGate : mobile carrier in some markets preconfigure iPhones to connect automatically to certain Wi - Fi electronic internet name .
These web names are easily spoofable , grant an iPhone ( or Mac or any Wi - Fi - enabled gimmick ) to connect to what is often scream an “ evil twin ” web . That web can attempt to cede malware or redirect to seem - like page among other natural process .
But it ’s often hard to overwork iOS unless there ’s an active , unpatched job , as is currently the case . The research worker report this to Apple , did n’t release the exact details of the establishment clangour , and iOS 8.3 appears to fix some , but not all , of the potential for exploitation .
Promiscuous Wi-Fi connections
Wi - Fi was educate so long ago that it carries with it a lot of cruft and difficulties . The first flavors of what is certified as Wi - Fi as an industry trade group were 802.11b and 802.11a , standardized in 1999 . Some aspects of that 1999 technology remains .
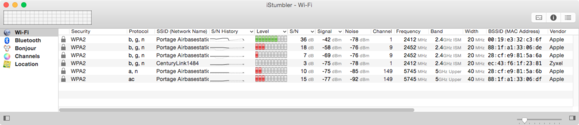
Every Wi - Fi base station and meshing adapter , as in a Mobile River or laptop , has a unique manufactory - assign name and address , just like every ethernet adapter . ( On some devices , that numeral can be change through software or firmware . ) A base place ’s computer address is a BSSID , or basic help set identifier , and it has a unique BSSID for 2.4GHz and 5GHz networks if it supports both at the same time or as an option at inauguration . These ID are represent as a set of six hexadecimal ( base 16 ) numbers separated by El Salvadoran colon , like 00:19 : E3:32 : D3:6F.
The $ 25 iStumbler utility reveals extensive details about all the Wi - Fi networks in the neck of the woods of a Mac , including the BSSIDs of each base post . ( Click to enlarge . )
But we do n’t , of course , link up to a base post by telephone number . Instead , we habituate a name , the Service Set Identifier ( SSID ) . In a mesh with multiple infrastructure place , this is called an lengthy SSID ( ESSID ) , in which every base place has its own numeric address but they all partake the internet name .
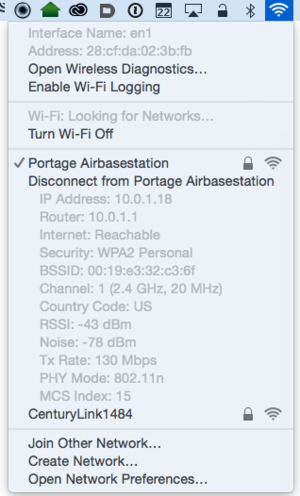
When you select the web name , your computer or mobile will examine all the base of operations station associated with the name , and pick one , typically based on a combination of signal lineament , signal strength , and throughput . Almost all devices freely roam , and unplug and reconnect as you move among as set of base stations with the same name . On a Mac , hold down Option and click the Wi - Fi menu , and the BSSID appears along with other connection parameters for the understructure station to which you ’re presently connected .
defend down the Option key and click the Wi - Fi computer menu , and you could see a number of parameters about the internet to which a Mac is connected , include its BSSID .
Here ’s the 1999 part of this par . For encrypted networks , your twist will only connect to a web for which it ’s store a watchword . If another web appears with the same name and a different password ( or even login method acting ) or without a parole at all , your gimmick wo n’t link up .
However , there ’s no certification or any sort for parole - free internet used for public space Wi - Fi in cafés , conference center , airdrome , and hotel . This is true even when there ’s a portal at which you ’re redirect to enter login information , a usance code , or defrayal particular . The net is still assailable .
This is an obvious problem , and has been for some clip . There ’s no way of life to prevent a equipment that has a stored net connective for an open net from connecting to any internet with the same name , regardless of which foot stations are attached .
Because fluid carriers have built up full-grown Wi - Fi internet of their own and partner with other internet for use to offload data ( and sometimes voice ) traffic from cellular meshing , a malicious political party can pick from among many networks name while also being assured in any dense dowery of a city of let a expectant attempt surface — M or tens of thousands of hoi polloi every Clarence Shepard Day Jr. .
The particular attack in question
The attack detailed by Skycure is entrancing because it apparently arise from only plug in a router that deliver a ill-shapen SSL certificate . This is n’t strange . A lot of connection power train is cheaply and hastily made , and uses generic and out-of-date microcode , sometimes thinly or unmodified open - beginning software builds .
The investigator found that their iOS devices crashed when colligate and sorted out the flaw . By using a similarly malformed certificate on an “ malign twin ” accession sharing the name of any of a number of democratic carrier - associated networks , an attacker could cause any iOS equipment that connects to doss down and restart .
But the rationality this flak is interesting is twofold . First , you do n’t have to have antecedently plug into to the Wi - Fi net ’s name in the case of meshing carriers bake into a visibility . Second , the crash happens at the initial connexion , so after reboot ( as shown ina videoon the house ’s land site ) the Wi - Fi electronic internet re - tie happens and the smash occurs before you may disable Wi - Fi on the phone .
Your only recourse is perhaps to enwrap the phone firmly in aluminum foil or leave the vicinity of the attack connection . To a even user , it would appear as if their earphone was simply broken and rebooting over and over again . Even restoring the earpiece in the neighbourhood would n’t work , because once it ’s set off on the aircraft carrier web , it would install or retrieve the connection setting profile .
And the onslaught is n’t active . With a bastard basis station set up , it demand no Internet connection and it can fake multiple names using virtual meshing , a Wi - Fi characteristic that lease one hardware floor station sport many public figure . ( That ’s how guest networking works with Apple ’s equipment . )
The repair is surely coming from Apple for the SSL certificate parsing fault . But the bigger issue in the diligence that remains requires time to prepare . There has to be a means to permit users more efficaciously only connect to networks to which they designate to , and none yet exists .