If you have n’t find out the termphishingby now , you ’ve undoubtedly live it . Phishers get off e - postal service messages design to trick people into forking over personal datum , such as usernames , passwords , banking company account number , social surety number , and more . Usually you receive an innocent sounding atomic number 99 - chain armor content — from your coin bank , eBay , or PayPal — that say something has get going incorrect with your account , or that you need to update some data . Somewhere in the organic structure of the message , there ’s unremarkably a link to your “ account status page , ” “ information update page ” or “ personal information page . ” If you cluck one of these links , the resulting Thomas Nelson Page mightlooklegitimate , as phishers expend steal mental imagery from the real situation . However , you ’ll really be on the phisher ’s internet site , not its legitimate counterpart . So how do you protect yourself ?
For starters , if you use Apple ’s Mail , you could force it to expose plain text only . This forces most phishing e - ring armor message to appear without links and images . ( Other chain mail applications may offer similar choice . ) However , since this means you wo n’t see look-alike or text styling inanye - postal service messages you receive , this approach is clearly not for everyone .
Another choice is to never sink in an unknown link in an e - mail — at least not until you know where that URL may go . gratefully , if you practice Mail in O X 10.3 or 10.4 it ’s astonishingly easy to see where any given link goes , even before you snap it .
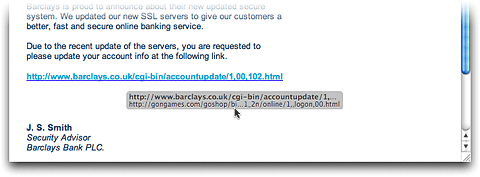
If you ’re running OS X 10.3 , just click - and - hold on the link for about a irregular , then start to drag the link toward your desktop . When you do , a small gray box will look , revealing the uniform resource locator behind the link :
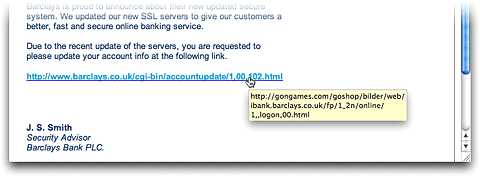
After you ’ve had a prospect to record the destination URL , just attain Escape to cancel both the drag and the tap the link . The only trouble with this method acting is that there ’s a opportunity you could accidentally click the inter-group communication while try out to view it . In OS cristal 10.4 , they ’ve fixed matter so that ’s no longer possible . There ’s no more clicking and dredge required — just hover over the link for a secondment with your computer mouse , and you ’ll see a pop - up give away the URL ’s destination :
Since you do n’t have to click the mouse button , there ’s no danger of accidentally activating the connection .
There are lots of phishers ( and scammers ) out there . But if you use a bit of common sense along with these link - check technique , you ’ll be well protect from their e-mail .