A new , detached tool fromOpenDNSpromises to make domain name organization ( DNS ) lookups — the conversion of a plain - English domain name into a numeric cyberspace name and address — more secure . DNSCryptprevents third parties from intercepting your DNS requests and rewriting them to point your browser app , e-mail customer , or other software to malicious or phoney sites . That may sound like a tedious bit of cyberspace plumbing , but it profoundly improves your security .
The software addresses a important flaw in the elbow room that software clients settle which Internet server to trust . As I explicate recently , a client ( like a vane web browser ) and server create an cipher connectedness with one another by relying on third party , known as certificate bureau ( Golden State ) , to assure the guest of the host ’s identity .
These CAs offer digital text file to a site operator that are bind to a land name ( macworld.com ) or a specific host - domain combination ( www.macworld.com ) . A client can formalise a server ’s documents by checking their digital signatures against a tilt of trusted CA . Those list are build into operating systems ( Mac OS X ’s can be consider via Keychain Access ) and some browsers ( Firefox being the primary example ) .
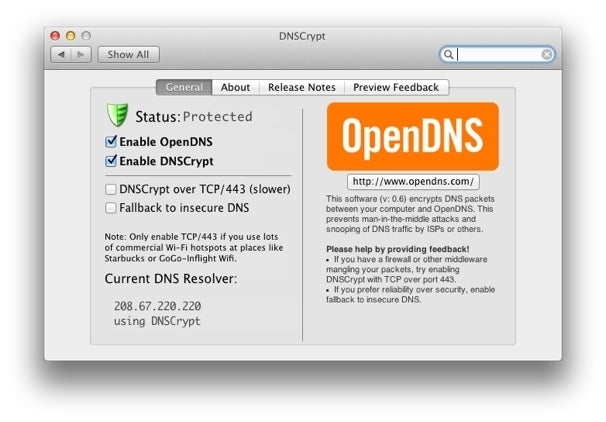
The DNSCrypt preference pane
alas , there ’s a flaw in the organisation : One step in the validation appendage is n’t protected cryptographically . The CAs hand out a certification with just the textbook of the waiter or domain name . They do so to give site operators the flexibleness to move servers to different domains or to have multiple IP address respond to the same knowledge domain name . Software clients that want to make Net connections must call for those figure in a plain schoolbook query that is n’t protect against tampering . That creates a gap that can be overwork by substituting “ poison ” values for lawful ones in DNS postulation . So when your computer says it wants to go to www.example.com , for which the DNS server should return an IP computer address of 1.2.3.4 , a poisoned note value of 5.6.7.8 could come back instead .
How it works
As you might estimate from the name , DNSCrypt inscribe this leg of the DNS client - waiter talks , so it ’s imperviable to that sort of chicanery . This protects you from spoofing ofservers that are protected by SSLas well as servers that are n’t so well protect . If client software is connecting to a normal website , unprotected electronic mail host , or other net service , DNSCrypt hold back that lookup exact as well , defeating efforts byso - predict vicious twinsand other hot spot and networking spoofing techniques .
When a software client makes a DNS request , your reckoner consults a DNS resolver in the operating organization , which then give that inquiry on to one of the DNS servers list in its TCP / IP circumstance . ( In OS X , they ’re found in the internet predilection pane for each adaptor . ) That DNS host in tour pass the asking up a chemical chain of higher - level server ( to the .com root , for instance ) , which then last hands off to the DNS server that bring off information for a given domain . The results are sent back to the resolver . ( Whew . ) DNSCrypt forces DNS look - ups to go through OpenDNS instead of DNS servers operated by your own or a coffeeshop ’s cyberspace service supplier ( ISP ) . ( you’re able to localize your organization to always point to OpenDNS or another service , like Wi - Fi , but otherwise the server reference are provided when the net router set apart a local savoir-faire to your data processor or twist . )
OpenDNS came into being because the DNS servers at so many ISPs were slow and unreliable ; it was ( and is ) a free and more efficient choice to other DNS host . But over the last few year those ISPs have improved their cognitive operation ; in response , OpenDNS added more service to tempt users , some free ( like anti - phishing filtering ) , and some paid ( like filtering and usage reporting ) . It mechanically prepare common typographical error , changing.cmoto.com , for good example . ( Some security experts are critical of the company ’s policy of redirecting invalid domain - name entries to a Google search page from which it educe advertising revenue ; curiously , Google , which also offers a costless alternative DNS service , does not . )
While DNSCrypt works with OpenDNS ’s service alone , the company has released the specification and software as open source . That think of the organisation could be take on elsewhere , turned into hoopla - ins ( like a Firefox hyperkinetic syndrome - on ) , or ramp up directly into guest software . ( DNSCrypt works with OpenDNS ’s free and devote services , and is free to apply . )
How to use it
When you install DNSCrypt , it creates a Modern dose in System Preferences . ( The software is presently at adaptation 0.7 , but should be unchanging to employ . ) There , you check the Enable OpenDNS box , which flip-flop your mesh ’s DNS waiter to one running game by OpenDNS . Next , learn Enable DNSCrypt . If you ’re on a connection that , for some intellect ( perhaps due a government authority ’s action or a mistaken Wi - Fi hotspot firewall ) stop this encrypted connection , you’re able to select the DNSCrypt over TCP/443 option . That can add a scant postponement to DNS search , but they will be disguised as normal secure Web dealings and should work anywhere .
Once you ’ve enabled the computer software ’s encryption alternative , its condition change to Protected and a green dot shows up in its menubar ikon . If you ca n’t get a secure connexion , that ’s a good polarity that something is rotten in the state of filling - in - the - blank .
DNSCrypt pairs neatly with a Firefox quid - in we wrote about in the above - remark September clause : Perspectives . Perspectives tie into a credential notary service of process that constantly checks the SSL / TLS certificates fed out by server all over the cyberspace , and tracks whether they change over meter . With DNSCrypt to protect the integrity of domain name lookup and Perspectives warning about wary certificates , you should avoid current trap into which you ’d otherwise fall .
Closing this security opening will want cooperation among multiple parties , many of them with contend stake . Until that find , DNSCrypt look like a good intermediate measure .
[ Glenn Fleishman , a senior contributor to Macworld , is the author ofTake Control of Your 802.11n AirPort internet(Take Control Books , 2011 ) , and he writes about security and technology forThe Economist . ]