Two late security incidents , WireLurker andMasque Attack , highlight both the ease and trouble of slip malware onto iOS . But they also show the way in which Apple may have infantilized its hearing into not knowing the right alternative to make when presented with a genuine security department fault .
WireLurker used malware inserted into Mac OS 10 programs made usable at a Chinese - focused third - political party app store to install apps to Io machine over USB . It add apps in jailbroken and regular devices . Masque Attack in its most powerful methodology pushes apps ( from websites , e-mail , and elsewhere ) that , if install , overwrite common popular apps and extract cached data for that app , such as Gmail . WireLurker has been in effect defanged;Apple has more work to doto remove any menace from Masque Attack .
But beyond their specific defect , they show the different paths taken with iOS and Mac OS X for app security measure . Apple has a split personality , partly rooted in history .
Two approaches
Apple did n’t ab initio plan to allow third - party apps in iOS , and when it opened the marketplace , it wanted to annul a deluge of malware , as well as keep out poorly made software that would go down the OS or burn cellular data . It also want a weapons platform that permit it control the stream of money change hands for apps and digital goods . It hold back that despite year of complaints , and both Apple and its defender often cite security as a major reason for keeping that tight control .
Apple keeps tight control over what go in the Mac App Store , but most software , at least by dollar value , still comes from outside the computer memory .
By contrast , OS X had its origin 30 years ago and through processor , architecture , and kernel changes , grow with the whim that anyone could write software that would run without outside permission . When the Mac App Store first appeared , there was a reasonable fear that Apple would transition from it being an option to being the only distribution method acting . That has n’t happened so far , in part because , by dollar mark time value , the vast legal age of software used on the Mac is from software system outside the App Store .
Yet despite the open nature of OS X and the wide handiness of non - App Store software , there has been no virally distributed or widely exploited method acting of hijacking a Mac or any of its software , despite many serious flaws and some malware discover in the wild . organisation design is n’t the exclusive answer : Apple has made good , but not always great decisions . Market part and a want of mechanisms to trigger multitude e-mail and automatically fulfil email attachments may have had more to do with it .
The nonintuitive Gatekeeper
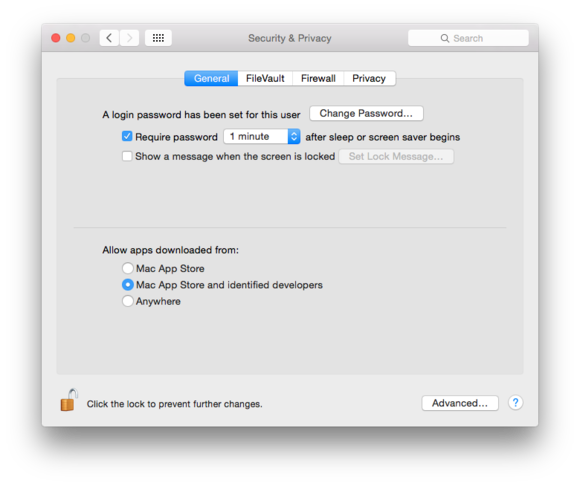
Apple seemingly trusts its Mac users , who may be no more advanced than the medium iOS user , to launch any package with a tiered approaching it sum in Mountain Lion withGatekeeper(part of the Security preference loony toons ’s General tab).Gatekeeperallows a user , or someone place up the system for a drug user , to select among three options that moderate which sorts of apps can launch in OS X : only from the Mac App Store , from the App Store plus discover developers ( those who sign their apps using Apple Developer credentials ) , and “ anywhere . ” Io lacks a direct analogue to this .
The Gatekeeper options in System Preferences > Security .
The default choice allows App Store plus signed apps , and a well - document but user - uncongenial method and presentment of open unsigned apps . three-fold - clicking an app with an “ unidentified developer ” results in a dialog that tells the user it can not be opened , but Control - clicking the app and selecting the Open point bypasses security . This subtlety is certainly beyond the ken of most user . ( A signed app that ’s been meddle with , or for which the developer certificate has been revoked , can not be instal through this method acting . )
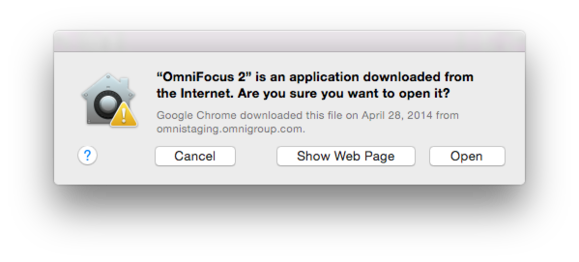
If an app from outside the Mac App Store is signed ( like this copy of OmniFocus ) , you’re able to click Open from this dialog . If it ’s not bless , you have to Control - cluck the app and select Open from the contextual card .
A friend , Kerri Hicks ( spouse of Bare Bones ’ founder Rich Siegel ) , explained to me recently that as the web managing director of a university , she is regularly consulted by other members of her team when they see the the Gatekeeper dialog . baffle , they come to her as the expert ; it ’s both nonintuitive and hard to train an mean user in the bypass . While I rarely open an unsigned app , Kerri enunciate it ’s a frequent occurrence in her field , which comprise spare , unresolved - source , and other forms of software in which developers may not want to take the time , spend $ 99 per year , or climb up through Apple ’s basketball game to get a digital signature bond .
An ad-hoc entrance to the walled garden
iOS also has a workaround , although it ’s extremely modified . Apple allows veritable developer to propagate test version of apps as “ ad hoc ” releases to up to 100 twist registered in the developer ’s account . Enterprise users , who pay $ 299 per year , can distribute apps completely outside Apple ’s process , but such statistical distribution is theorize to be restrict to employees of the firm with the account . ( TestFlight is another selection for software examination , now owned by Apple , but Apple handles statistical distribution of loss . )
An ad hoc app is unbelievable to be found in the wilderness except in very special attacks , because of the unique equipment limit : without the UUID of an iOS gimmick , an app sign with the ad hoc credential ca n’t be install . initiative - signed apps were used in WireLurker and are most of the threat of Masque Attack , although it ’s possible “ spearphishing ” ( highly targeted attack ) could make employment of ad hoc provisioning as well .
In both cases , though , either when download or installed , such apps command a drug user to O.K. them , with one or two stride , pink Install or Trust at a prompt that provides piddling information and none of it validated — a malicious developer can claim to be installing “ New Flappy Bird ” and instead overwrite any non - Apple app . ( Apple can centrally revoke any go-ahead certificate , which has close down WireLurker , and make it quite difficult to use the Masque Attack , as once it ’s discovered , an improper or hijacked enterprise developer account can be disabled along with its certificates . )
Users need help to make smart choices
Which brings us to the crux . Mac OS X countenance any arbitrary app to be installed , has been resistive to widespread malware , and render paths that allow selective security for vary degrees of abidance with Apple ’s mandates . But most users require account to install unsigned apps unless they fully disable Gatekeeper , which is inadvisable . iOS resists installation of apps that are n’t in the App Store , but seemingly gives naif user little information about making a full alternative when faced with unexpected prompting .
After Apple bought TestFlight , some developer flip to Hockey App for pass around ad hoc software for iOS . Not a lot of multitude take these ad hoc apps , but the process for clear and instal them can be confusing .
It seems like Apple could tighten and loosen app security at once without compromising its purport or users . Relatively few users need to set up ad hoc or endeavor apps , and it should provide vindicated steering in iOS — and maybe a mode to turn off such installing without an additional security basketball hoop being jump over . Likewise , OS X could make it wanton , or at least clearer , how to overcome Gatekeeper when one needs to .
But the experience with OS X and these two malware endeavour should also provide guidance in tease apart the reins of iOS . The two exploits are all thwarted by the difficulty in obtaining endeavor certificates and the ease with which Apple may revoke such encoding written document . crack up iOS open to supply a Gatekeeper selection for signed apps only that have verified information and of which drug user has to okay the installation and launch would still give Apple a way to close malware down quickly .
Apple ’s unlikely to give up its fixed iOS control , but it ’s ironic that malware break how well OS decade manages wholeness , and how easily iOS could be extended to gain users and developers alike .