Yahoo is trying something Modern : telling its user to go around a parole entirely in favor of a smartphone app through which a user grants access when a login is attempted . This seems like , in the password of one Twitter wit , two - factor certification ( 2FA ) with one agent . Is Yahoo ’s Account Key offer a unknown determination that will badly affect the security of those with accounts in its connection ?
My aboveboard answer is : No . Yahoo want to make it easier for its users to have the benefits of authorized logins while reducing the public utility company of stolen password to bad thespian , and it take a method that ’s better than watchword in virtually all consideration . substantial Book , I know ! I do n’t expect other companies to survey immediately , but Yahoo is essay to stand up out .
It ’s borrowing a pageboy from more advanced system , likeDuo Security , which has a more complicated setup and is contrive for corporate - scale security , but hire the same introductory principles . Yahoo is land this idea to the pot who can use existing apps to take vantage .
The key factor is a lack of password
permit ’s break down how its young Yahoo Account Key system works . I ’ve essay it , and it works just like Yahoo aver it should .
First , you instal their newiOS app for Yahoo Mail . Account Key works just with this app and logging into Yahoo on the WWW , but will be rolling out to other apps this year , the company saidin a web log post .
Next , lumber in with your username and word . You ’re essentially turn the app into a trust twist — a la Apple ’s old two - step and new two - factor system — and thus you have to award current info . Next , wiretap the visibility icon at the top of the filmdom and pink place setting . pat Account Key and you may start the service . Yahoo wisely walks you through a demo of accepting and rejecting connections so you may practice it . This is authoritative for its objective exploiter for this feature .
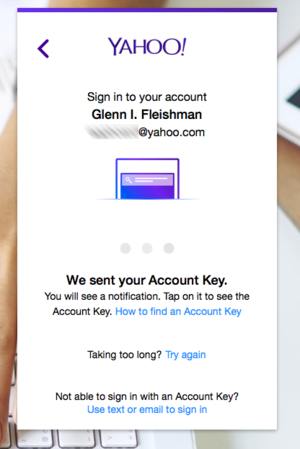
The Yahoo website transcend the login approval to a smartphone app , offering alternatives if it does n’t work out . Once approved at the app , the login completes mechanically .
In my test , I pass away to Yahoo.com to lumber into my email account . I entered the savoir-faire , and it intelligibly immediately recognized I had Account Key combat-ready , as the countersign field change to read Click to Use Account Key , and the Sign In button transform to scan Continue . A concealment on the internet site says its wait for favourable reception , and your iOS equipment sends a notification that give to a view that lets you agree to permit the enter or not .
Login attempts show up as notificaitons if you ’re not in the app .
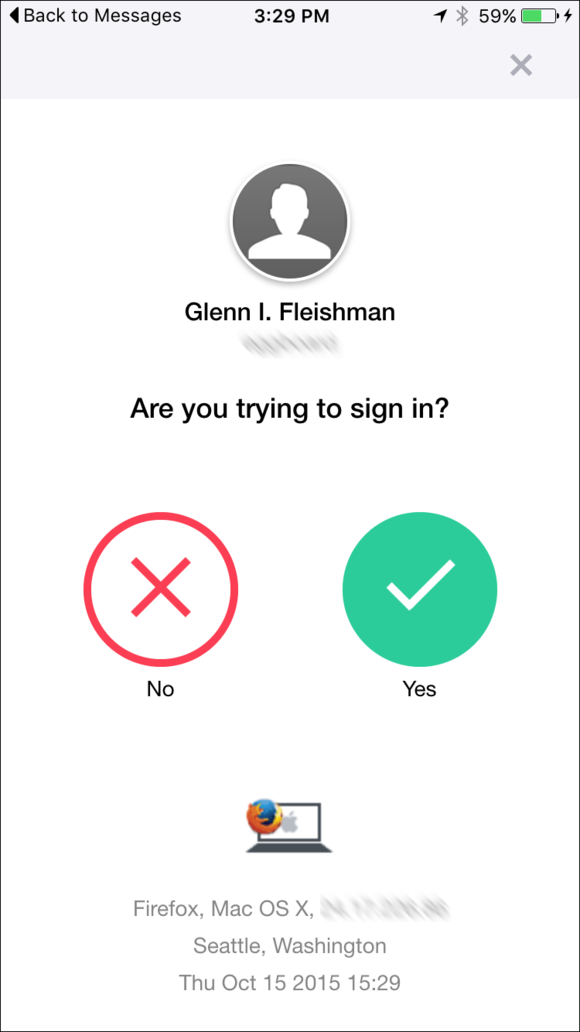
The Yahoo Mail app prompts you when a login attempt happens elsewhere . You ’ve given a fortune of contextual information and a grown reddened X if it ’s not ok .
To more experienced drug user , perhaps this all seems too superficial — how can this preclude a ne’er - do - well from access your account if all they call for is your word to set up an iOS app ? But the interplay is much richer than that .
True : You have to begin by using an existing password . However , there ’s no way of life to exploit this en masse shot . As with many kinds of story security department issues , there ’s a strong divide between being able to attack an case-by-case target ’s account ( for theft , harassment , felonious grounds , and more ) and have vast cumulation of passwords that can be used to attack giants peck of account .
I can get it for you wholesale
Yahoo release a logarithm in into a “ retail ” transaction , where someone has to prevail your bill name and password , secure those into its app on an iOS or Android twist , and have all the tracking associated with that .
Once past the login stage , not having a password isso much more securethan having a password for a large number of people . Normal human beings pick easy - to - call back passwords , which are in go well pretend or crack . They also often provide passwords when phished through email or even grifted over the earpiece . Without a countersign , there ’s nothing to slip — except the physical equipment on which the Account Key choice is enable .
This shifts the flak burden to physical proximity and personal knowledge . Someone who wants to break into your Yahoo email bill ca n’t do so remotely : They have to be near you . They ca n’t do so softly by just having approach to your computer : They need your phone , and the phone has to be unlatched . If you have a passcode , they have to approximate or know the passcode ; with Touch ID , they need … one of your fingerprint . And they ca n’t do so without a trace : These connections are lumber by time and day of the month and IP address .
For a user who does n’t want to compile unmanageable passwords and want less risk of remote attack , Yahoo ’s glide path is honestly superb . It ’s also just apparently simpler than not just two - factor logins , but even logins with passwords , which could lead to extensive borrowing by its users . It get less clip with a greater self-confidence and actuality of security . The fillip is that it makes any Yahoo security system boner less significant , so long as the Account Key interaction is want for logins .
Now , some people require the extra security of a two - footprint or two - factor approach . In both cases , a countersign is still required , although it does n’t have to be as stiff as when used in closing off . A second step ( sanction a connection from a trusted gadget ) or a second factor ( a unique bit of information not usable via the same login path).Apple ’s fresh two - factor(but really two - step ) system first asks your favorable reception for a remote login by showing its boisterous location and requiring you click Allow ( or Do n’t Allow ) , before it feed you a codification to use to supplement the password footfall .
Having two footstep or divisor aggregate something you know ( the watchword ) , which might never be crack or uncovered , with something else ( a time - based one - clock time word , an SMS - delivered codification , or something an app generates ) that has to be hold . But for most citizenry , the gulf between what Yahoo is offering and a plain countersign is enormous , and a rise .
I ’m looking ahead to more straightforward variants on Yahoo ’s schema that dislodge cracking from global to strong-arm proximity while also making it a good process for people who do n’t want to manage their security measures , while still benefiting from it .