If you read this column at all , you have a go at it I ’m a big fan of two - factor assay-mark ( 2FA ) , a password - plus - a - matter method of reducing the peril of other people and malevolent parties gaining access to your accounts remotely . But a care relate to deploying a 2d component on accounts that allow it ? Losing it !
In a recent conversation with tech - savvy co-worker , I found that a surprising number were concern that enable a second gene could pull up stakes them vulnerable to a organisation crash or a broken or lost sound that contains a necessary token or hole-and-corner . Without that , they worried about being permanently locked out of their hooey . This is totally reasonable , and you may create a plan when you bug out using two - factor logins to prevent this from happening .
As a speedy reminder , two - factor systems almost always pair a password with something else that you keep in law of proximity : a twist that take in a code , or an app that generates a computer code , or even a biometric machine like a fingerprint reader . The 2nd codification or physical detail reduce the opportunity for someone to obtain your password and then attain full memory access to an bill . Some systems are more accurately two pace , as a two - gene arrangement should n’t require an chemical element that is n’t also stored or otherwise connected with password entry .
Back up to get started
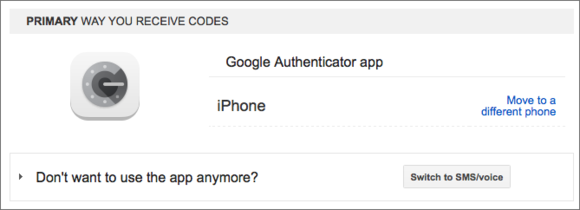
Systems that use the Google Authenticator approachof seeding what ’s called a “ Time - ground One - Time Password ” ( TOTP ) offer a QR code when you enable this form of supplementary protection that you’re able to scan with your phone or tablet . Some also provide a text - based equivalent weight .
Google have you set a lot of parameters around a 2nd factor , and deepen your psyche once you have .
These source computer code are used as the footing on both the account system you ’re using and in your own certification app to generate the TOTP . But you’re able to also enamor them and store them securely so that if you fall behind access code to a equipment containing the app or it crash irrecoverably , you’re able to reseed an authenticator with that same seed code . you’re able to screen gaining control or take a picture of the QR computer code or copy the text . ( To decipher the QR computer code into text when it ’s not included , you could use a reader likeQuick Scanfor iOS . )
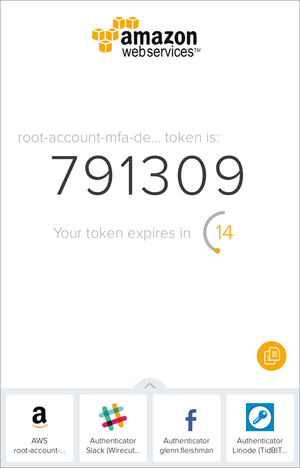
you could also expend apps that back up and synchronize your codes , though there are good rationality to think whether it ’s wise . Authyis a bare multi - platform scheme compatible with Google - manner TOTPs that optionally allows synchronization . The basic apps and functionality are destitute . AgileBits’1Passwordadded TOTP support in early in 2015 , and like other items in the program , they can be synced among gadget .
Keeping electronic copies of the seeding codification or sync it precede risk , but the key reward of TOTPs is that a exclusive password is no longer your only business line of DoD . ( AgileBitsexplained this wellin announcing TOTP support . ) Because Authy and 1Password do n’t stash away your information in a mode they can decrypt , with a secure word ( and optional exercise of Touch ID ) the TOTPs are locked away with a high degree of security . If you store screen door captures or picture or codes or the underlying text , make certain you practice a standardized encryption process to prevent entree .
Setting a path to recovery
Authy study TOTPs and optionally syncs them across equipment and platform .
Every site with any kind of two - step or two - factor system offers a way out when you ca n’t get back in . It can vary quite a bit . The most popular admit the pursuit :
Backup codes . Google and other sites make a list of static one - time purpose codes that will provide access , but ( as their name describes ) ca n’t be used again . These can also be good to use when you ’re by from a entrust computer , because they ’re fully unplug from app - generated TOTPs , and ca n’t even be used again with the typical one - minute - upper limit timeout for TOTPs . Many sites recommend publish out these stable code and carry them with you for vital business relationship . You could store them in an inscribe form on a local gadget , but that adds risk unless the countersign is potent and unique from anything you utilize online . The key constraint is to ensure that someone who could grab your password remotely could n’t also gain access to these one - clock time exercise codes .
substitute email . Some sites will let you recover approach by netmail to an account , which might be your chief email already colligate with the web site , or might be ask to be a separate speech . This ostensibly reduces the betting odds that a single full stop of nonstarter on the same path allows a third party to gain access to your 2FA - protected account .
Recovery Code . Apple ’s two - step verification system , which isbeing phase outin favor of its iOS 9 / El Capitan 2FA plan of attack , issue a alone code when you register to habituate it . That code is the only pick for recovery in the event your account is locked due to security measure concern , or if you lose admission to all your trusted devices and associated headphone numbers game . ( With Apple ’s 2FA , which is still technically two - step in nature , Apple has a human - involved recovery process you bulge out in the unlikely outcome you ’ve lost everything . )
Many sites use Sm to send one - metre employment codes , making it vastly less likely you ’ll fall behind full access to that “ factor”—your speech sound number . In most countries , a cell carrier controls access to a phone number that can have text messages , and a missed or steal speech sound is an inconvenience that demand bugger off that unit disabled , and having the phone numeral trip on another . My married woman and I add each other ’s phones where possible as additional backup .
In some relatively rare causa , you might lose control of an account , and when you want to get that number restore , a attack aircraft carrier might be unconvinced that you ’re the legitimate owner . More commonly , if you ’re using an alternative SMS organisation , such as Idescribed in a column in October , you might suffer access to the number and have no recourse to obtain it .
So when set up any SMS - based factor , ensure there ’s still another way out if the phone number in inquiry were to become unaccessible to you incessantly .
One step after another
With Amazon sum up 2FA support for regular consumer accounts , and Apple emphasizing availability during iCloud account setup , a circle more people will be using 2FA in the future . If you had concerns , I hope these help alleviate them , and you’re able to use this info to gruntle others ’ fear , too .