First , the bad news . Once again , Mac users are at risk due to a defect in Java , standardized to the one that enabled theFlashback Trojan . Even worse , there is n’t ( yet ) a patch to pay off that vulnerability . But do n’t care : This sentence around , there ’s good news for Mac users : Thanks to changes Apple has made , most of us are likely to be safe from this threat .
That aver , although you likely are n’t at risk today , it is clear that Java still represents one of the big , most lasting security problems facing users of all operating system . So I advocate you consider implement the precautions suggest below .
What happened
On Sunday , August 26 , security marketer FireEyepublished information about a raw Java attackthat used a antecedently strange Java vulnerability . The attack , which originated from China , strike the latest interlingual rendition of the Java Runtime Environment ( Java 7 , version 1.7 ) . The approach comes through your vane web browser app when you surf to a malicious site and allows an attacker to silently take complete ascendance over your computing machine .
After FireEye ’s initial stake , details about the vulnerability quickly became public and exploits taking vantage of it seem in multiple attack tools . Further research by security vendor Immunity Inc. indicated that the participating feat actually took vantage oftwo disjoined unpatched Java vulnerabilities(what we , in the industry , callzero - day ) .
The exploit for the first exposure wasquickly added to the BlackHole using kit — one of the most wide used malicious hacking pecker . The exploit is also now uncommitted as an attack inthe Metasploit insight - testing theoretical account , which is freely usable and favored by script kiddies and security measures professional ( myself include ) throughout the cosmos .
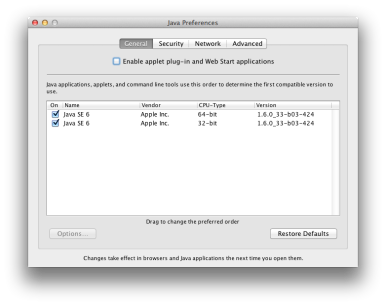
This is what you want your Java Preferences to look like.
At this time , Oracle — which inherited Java when it get Sun Microsystems — has not commented on the exploits , although we now roll in the hay that the companyknew about the vulnerability since Apriland was plan to unloosen a patch in its October update . Only time will tell if the company will break its quarterly spot bicycle and liberate an parking brake update preferably . ( My money is on other release . )
In sum-up , we have at least two exploitable vulnerabilities touch anything running the late edition of Java , both are being used in fighting attacks , and one is bundle with one of the most popular spoiled - guy rope toolkits on the market ( BlackHole ) and a very popular ( and barren ) security examination tool . You ca n’t patch up either one .
It ’s the very definition of “ bad ” .
Why most Mac users aren’t at risk
All that said , there are two ground why Macs are less at - risk than people on other platforms , despite beingeasy to tap if the right conditions are in place .
The first , and most important , reason is that comparatively few Macs are start the vulnerable variation of Java . Any operating system running JRE 1.7 is affected , but the attack does n’t work out against JRE 1.6 . That last one is the interlingual rendition that Mac users have set up ( assuming they expend Java at all ) .
Theonlyway to update from Java 6 ( 1.6)—the last adaptation supported by Apple — to Java 7 is by manually downloading and installing it from Oracle . And apparently few Mac drug user have done so : For example , according to a congressman of Crashplan , the online backup man avail that habituate Java for its client app , noneof that party ’s user ( who must have Java install ) are using the vulnerable interlingual rendition .
The 2nd ground you do n’t have to worry , even if you do have Java 7 set up , is that Apple by default option handicapped Java applet support in Web browsers in its most recent Java surety update . originate with OS X 10.7 Lion , Java is n’t installed by default anyway . And even if you do turn on Java , OS X will turn over it off again if you do n’t use it for a while .
Many user do set up Java for websites or applications ( like Crashplan ) that require it . But , again , even if you did instal Java , the odds are very , very good that you are n’t running a vulnerable translation .
What you should do
There are two simple room to check to see if you ’re vulnerable to this late terror .
The first option is to start the Java Preferences app ( /Applications / Utilities/ ) . On the General pill it shows the version of Java you have set up . If it says you ’re operate Java SE 7 , and if the Enable Applet Plug - in and Web Start Applications option is checked , you are exposed . If it says Java SE 6 , or if that applet option is n’t checked , you ’re good .
you’re able to also check your version by opening Terminal and typingjava -version . This time you require to make certain the reception isn’t1.7 . If it is , do n’t be too alarmed ; you ca n’t be work if you do n’t also have that web internet browser funding turned on in the Java Preferences app .
If you are vulnerable , straight off uncheck that Enable Applet Plug - in and Web Start Applications option in the Java Preferences app . Doing so is n’t a perfect defence , but it does preclude malicious website from exploiting you . (
You could still be fox into downloading an exploit that you would run manually . )
Using the Java Preferences app is more honest than incapacitate Java in your web browser app since it blocks it fromallbrowsers at once . This allow you to still use Java on your Mac , but without the risk of exposure of being infected through your web browser app .
The safest way to keep using Java
If , like me , you still involve to use Java in your web browser app , I recommend the following steps . They will reduce your risk , and I recommend them as an ongoing protection practice even if you are n’t on the vulnerable variation of Java . Because , to be dependable , these Java attacks are n’t about to slow down down anytime before long .
First , manually disable Java in your Web web browser app . Even if you turned it off in Java Preferences , this will keep it from running if you ever alter that setting ( which we are about to do ) . In Google Chrome typechrome://pluginsin the destination Browning automatic rifle and penetrate the link to disable Java . In Safari , go to Safari > penchant and uncheck Enable Java on the Security pane . In Firefox go to Tools > Add Ons > Plugins and uncheck Java Plug - In .
Next , re - enable Java applet support in the Java Preferences app ( or wait for your Mac to automatically propel you the next fourth dimension you need it ) .
Third , pick a secondary web web browser that younever usually useand re - enable Java in it . For example , I use Chrome as my basal browser app , and I disabled Java in it . I almost never use Firefox , but I still have it set up and Java is enabled in it . This protects me as I graze around the Web . ( I also use Safari for development examination , so I keep it handicapped on that ) . Whichever web internet browser you choose as your secondary one , you should apply it only when you acknowledge you need to use Java and you are going to a site you know . For me , I mostly require Java for demonstrate webcasts , so when I hit a web site I must use that requires Java , I apply my backup web web browser .
Disabling Java in your daytime - to - day internet browser and have a second web internet browser for Java needs is n’t perfect , but it does offer a tidy sum of protective covering . It ’s easier to remember than establish a cock likeNoScriptwhich block Java on private page , but which many non - techie users get hold cumbersome . ( I really lead it in Firefox , as another layer of protection , but I ’m a tantalize security geek ) .
Another choice is to get at Java sites only from inside a practical machine . I runVMWare Fusion ( ) ( and sometimesParallels Desktop [ ] ) and frequently utilize Windows practical machines for inflict those non - Mac - compatible websites I sometimes need for employment ( again , unremarkably old webcast organization ) . I keep a baseline shot of my practical automobile , and turn back to those after any risky activeness .
We dodged a bullet
For once , being a software translation behind worked to the vantage of Mac users , and well-nigh no Mac user are really at jeopardy from the late Java exploit . But , as we ’ve seen with Flashback and this late attack , Java remains a prime object . Thus I ’d commend that all drug user protect themselves , even if you are n’t presently at risk . Disable Java if you do n’t need it , grow it off in your browsers if you do n’t want it there , or only use it under controlled circumstances if you do n’t have a choice .
Rich Mogull has worked in the security macrocosm for 17 years . He writes forTidBITSand work out as a security psychoanalyst throughSecurosis.com .