Making the connection
The table service also require either a public , routable IP destination — a rare particular on home connection and most work networks — or a broadband or Wi - Fi router that affirm one of two larboard - mapping protocols noted just below .
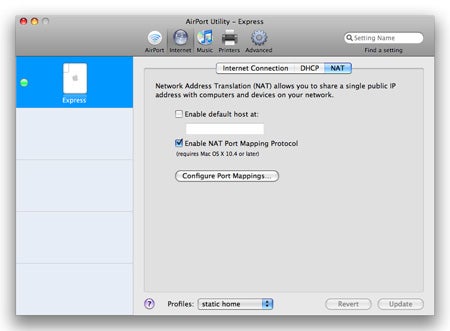
For other Wi - Fi and broadband routers , confabulate the manual of arms for UPnP and how to turn it on . In many case , it may be enabled by nonpayment .
In any Finder window , the sidebar ’s shared out section will show your computer using its Computer Name as define in the Sharing preference pane . ( If you do n’t see the other information processing system you ’ve enabled in this list , you may need to wait : Apple ’s still meliorate the help to work with more router and web peculiarities . ) To use outside divine service , stick to these steps :

For file sharing :
For screen sharing :
Security concerns
For the very proficient , this new public utility hides the even higher complexity of a command - line prick receive in Tiger .
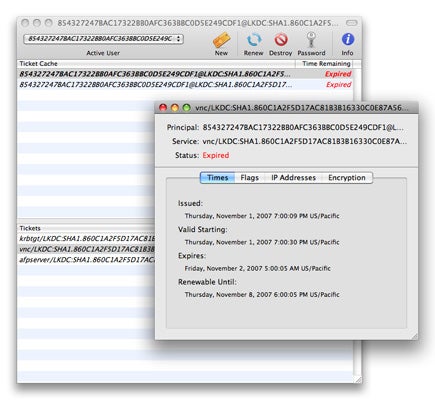
you could use the Kerberos Ticket Viewer to delete tickets and extend their lifespan .
Despite these substantial measurement , there are concerns about how the .Mac password winds up being the root for much more secure measures .
Rich Mogull , a security system research worker who turn tail theSecuriosis web log , said via e - mail , “ I ’m just uncomfortable with using security - only authentication to allow full remote admission to my organisation . If they only added a password prompt for the outback system ’s password , I ’d be happy . ” Mogull pronounce he prefers at least two - constituent certification , in which two dissimilar elements are required to gain approach , each of which has separate security measures mechanisms to protect the secret .
Final thoughts