“ Phishing ” is a cute name for a malicious practice session . An assailant mail millions ( or even a billion ) of emails that tries to convince someone it ’s from a logical informant . Phishing sometimes rely onthe billions of account compromisesthat have occur over the last several years to include telling personal details , like your mailing name and address or an account name associated with a site .
The chain mail win over you something is wrong with your account , or there ’s a with child promotion afoot , and press you to come home a link that looks correct . Clicking brings you to a website that wants your account credential . Proceed — and you may have given away the keys to your kingdom .
This kind of tone-beginning is insidious because most of us receive so much email from companies and organization we deal with that we can barely bring off all of it . A message that say “ credit rating calling card exceeded limit ! ” may rise above the fray , and you yield attention . The site to which the email is associate looks just like what you wait .

Safari warns of connections to sites that aren’t what they appear to be—but you’ll see it on a hotspot network if you haven’t yet passed the portal page.
I address from a position of a fellow sick person . Over the last year , I ’ve received a text edition substance from “ DHL ” and two emails from “ American Express ” that virtually got me . I clicked the DHL message , as I was anticipate a package from that inspection and repair , which is rare for me — and quickly realized what I was doing and close up the windowpane . With the Amex substance , they both meander up filter into my junk e-mail booklet , but I looked at them and cerebrate , “ This must be in error . ” However , on nigh exam , I realized my spam app was more observant than I was , and I never clicked at all .
Here ’s what you’re able to do to reject these attacks in an email message .
Disable loading images
unseeable tracking pixels allow both seller and scammers to fuck a message was opened and may let on more than you want about yourself . You canfollow these instructionsto disable automatic image and medium loading . start up with the discharge later this year of iOS / iPadOS 15 and macOS 12 Monterey , you’re able to go further by enablingMail Privacy Protection , which loads tracker through a placeholder to go the connectedness to you . ( This feature does n’t require iCloud+ , the new name for pay iCloud tier . )
Don’t click on site links in email
While it ’s convenient to sink in links in electronic mail , notclicking nexus and instead using bookmarks or typing the first few letters of a situation bypasses most phishing attacks .
Hover over links before clicking
If you ’re thinking of tick and have an email customer ( like Apple ’s Mail ) that supports it , you could hover over any link and see what it appear like . If it ’s not the URL of the party or group who sent it , do n’t snap . Some company use email tracking and route their link through Mailchimp and other logical e-mail - sending house . But you ca n’t differentiate between use and misuse in those cases . With Apple e-mail , levitate over show the URL as tip text ; only when you come home the downwards - pointing arrow do you get a full prevue , which I recommendnot doinggiven the risk of providing more data about yourself .
Look for warnings in email
Some e-mail apps automatically monish you or you may enable warnings that tell you a message wait mistrustful or has links to point to known phishing sites . I use Postbox , which has this choice . It ’s not always accurate — it dislike eBay ’s emails for some reason — but it at least makes me warier of an incoming e-mail .
If you decide the link is legitimate and go out front and chatter it , be wary and trace this advice :
The one occasion in which you will see an erroneous belief when you ’re seek to visit the lawful version of a site is when you ’re at a public hotspot and have n’t yet jumped through their hoop to conjoin the connection . When you touch base to such a hotspot , it obstruct worldwide Internet dealings . It efficaciously redirects everything to a local “ portal ” Sir Frederick Handley Page where you’re able to pay , go in a login , or concord to terms of service for free access code .
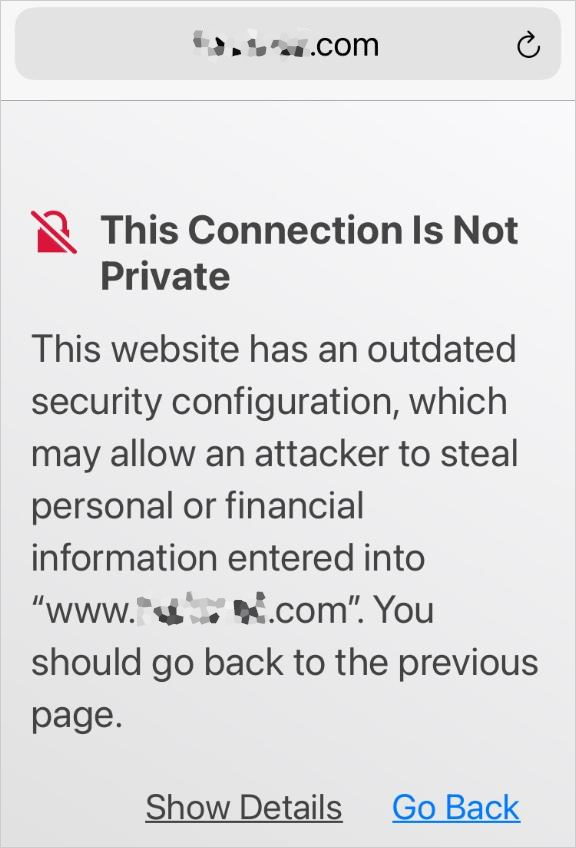
Safari warns of connections to sites that aren’t what they appear to be—but you’ll see it on a hotspot network if you haven’t yet passed the portal page.
Until you fade the portal Sir Frederick Handley Page , any other entanglement page you call in will produce an mistake that look like you ’re at a fallacious land site .
This Mac 911 article is in reply to a motion posit by Macworld reader Tom .
Ask Mac 911
We ’ve compiled a list of the questions we get take most ofttimes , along with answers and link to columns : read our super FAQ to see if your question is covered . If not , we ’re always take care for young problems to solve ! Email yours tomac911@macworld.com , including screen door captures as appropriate and whether you require your full name used . Not every question will be answered , we do n’t answer to electronic mail , and we can not provide direct troubleshooting advice .