As reported Wednesday , there ’s a new piece of OS disco biscuit malware in the wild — a Trojan Horse that change your Mac ’s Domain Name Server address . We ’re already cover how to detect and remove that particular piece of malware . Now let ’s turn our attention to what you may generally do to forbid such things from getting install in the first place .
observe that this is a discussion focus on trojan horse malware computer software in particular — computer software that profess to be one thing , but is actually something else , typically a program with malicious spirit . The general practices , however , could be apply to nearly any sort of program you download .
The things I ’m going to demonstrate — with one small exception — are also Terminal - free , and require little to no technical knowledge . In myopic , anyone should be able to habituate these technique to examine downloaded programs before installment . Note that this walkthrough is longsighted and elaborate ; here ’s the executive summary edition :
Control - tap the installation parcel and choose Show Package Contents . sail into the various files within the installer , and look at each in a school text editor . Some may open as gibberish , which indicates that they ’re binaries . Close those files . For the files you may register , expect for anything that just does n’t make sense . If you find even one thing that seems weird , do not deploy the syllabus .
Read on for a more elaborate spirit at the operation of essay installers .
Rule #1: Avoid untrusted sources
Really . I mean it . Stay off from untrusted sources . If you on a regular basis ignore these two rules , you really should endow in some good anti - virus / malware software . It ’s not perfect protection , but it ’s a lot better than flying unreasoning .
But what if…
OK , so somehow , through no fracture ( or all flaw ) of your own , there ’s a disk image sit in your Downloads leaflet . You ’re pretty trusted it ’s legitimate , but you did find it on a not - well - known site , and you ’d like more of a tender - and - fuzzy touch sensation before you take the risk of installing it . You ’re not an extremist - geek with l33 t Terminal skill , though , so you may think your pick are limited .
I ’m here to tell you that ’s not the case : with just a text editor and the power to learn English ( assume we ’re talking about an English app , of course ) , you could in reality do quite a bit of snooping on your own — all without ever running the program in dubiousness , or requiring any proficient attainment beyond the power to chatter the mouse button .
I ’m going to focus today on program that come as package installers — these are the programs that run with Apple ’s installer , and many will involve for your admin password . If you supply it , you ’re essentially granting the curriculum the right hand to do anything it wants to to your Mac . As such , these are the programme you should be most implicated about . ( even covering can be malicious without requiring your admin password , of course , but they ca n’t establish things in home where your user can not do so without authenticating . A bundle installer with your watchword can put anything anywhere , and change anything it wants to . ) The crown I provide here , though , are useful for seem at any variety of programme you ’re going to install .
To demonstrate the differences between a malware bundle and a normal packet , I ’ll be using the literal installer for the OSX.RSPlug . A Trojan Horse ( RSPlug . A for short ) , and Microsoft ’s Modern Remote Desktop Connection 2 genus Beta 2 ( RDC2 ) . As you understand the following , call up that the malware packet was aim to be an installer for a video codec , to aid you watch some on-line picture . ill-use with me now , into the wonderful world of package installers …
About packages
Package installers are a lot like covering in OS X — they’re booklet disguised as something else . As such , they can be unfold and search , which is the key to quash malware installation on your machine . But even before you get to that decimal point , there ’s a fair bit you’re able to figure out just by look at the installer ’s disk image mounted on your Mac — so that ’s where this exercise starts , by mount the questionable disk prototype .
crucial short letter : Everything that I ’m about to show you may be mould around by a dedicated malware author ; there ’s no warranty you ’ll always find these “ William Tell , ” but there ’s one thing make in our favor — malware authors are normally interested in getting their material out as quickly as possible . That means they ’re credibly not snuff it to invest the clock time necessary to do all the item body of work postulate to disguise their cartroad — so you may very well witness this data utile for succeeding sleuthing . Please do n’t take any of it as a warrant , however .
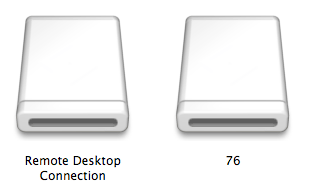
With that note in intellect , now consider the two icons below , with Microsoft ’s RDC2 on the left field , and the RSPlug . A malware on the right .
Notice how the Microsoft disk image has a “ real ” name , while the malware is advert simply “ 76 . ” That should be a somewhat good clue that something ’s not right already — very few Mac programs are named with bit and nothing else . Obviously , malware writer could take the time to think up a phony name , but that ’s the point — it take time , so they may not make the effort . If the name of something does n’t depend right , that ’s your first clue that it may not be right .
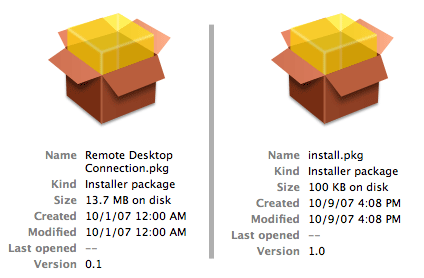
Next , allow ’s examine the detail on the parcel on each disk image . Here ’s a shot of each , as taken from the preview in tower position mode :
There are two things here that catch my eye . The first is that — even if you accept that “ 76 ” is the name of the political program — detect that the name of the actual installation program on the disk figure isinstall.pkg . This does n’t match the name of the disk image , nor does it seem like anyone serious about their software would unloose an installer named simply install.pkg . Compare that to the RDC2 image on the left wing , where the name of the installer match the name of the disk image , which match the name of what you think you ’re instal .
While you ’re looking at this disc double , comment the Size entry . RDC2 is 13.7 MB . Not flyspeck , but not huge in today ’s world of multi - gigabyte game demos and 350 MB software update downloads . Now face at the size of the install.pkg on the right : 100 KB . I took a look at MacUpdate and sort out its filing cabinet list by size . Out of 1,300 programme that appear in the list , only about 50 are 100 KB or smaller . I then searched on “ codec , ” and only two of the 23 lucifer are under 100 KB . Most of the video - related codecs are in the 3 M to 10 megabyte reach . Simply put , 100 KB is too small to be a genuine video codec .
But you do n’t have to do all the searching I did to know that something ’s haywire with the size of this bundle . Think about everything you ’ve download lately , and how many of them were under 100 KB . Excluding text Indian file , the answer is believably none .
So while we have n’t even really set out looking at this software system yet , it ’s already amaze three strikes against it : 1 ) The disk image has an unpaired name ; 2 ) the installment software ’s name does n’t match that of the disk image ; and 3 ) the size is too minor to be logical software . At this spot , if this were “ real life , ” I ’d scrap this disk image immediately ; it only can not be what it purports to be , so the odds are high that it ’s something that I really do n’t need to instal .
Diving into packages
But this is n’t real life , this is the World Wide Web , so we ’ll keep digging . By canvas the content of the facility package , you could usually encounter all the grounds you want to convince yourself as to the legitimacy of a given program . Just keep my cautiousness in mind — it ’s possible that a well - develop piece of malware may not have any of the following “ tells . ” Still , it never hurts to take care .
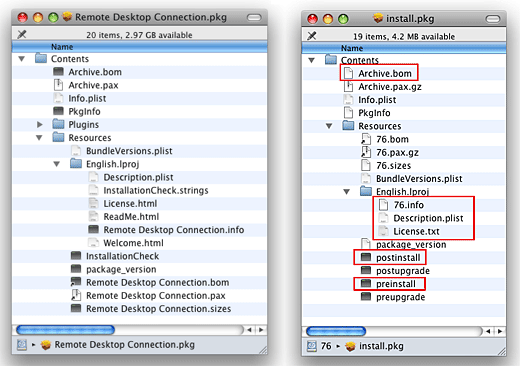
control condition - get through on the installer software program in the Finder and prize Show Package Contents from the down - up menu — you’ve now “ entered ” the installer ’s bundle of files , and it ’s here where you ’ll really bring out what makes up this particular programme . Here you’re able to see both the valid RDC2 package ( on the left ) and the RSPlug . A trojan ( on the right ) .
You really ca n’t learn much at this level yet , but here ’s the significant bit : Many of the filing cabinet in an installer software program are text Indian file , even if their icons do n’t look that direction . So one way to explore is to scuff and shake off each image onto a text editor , and see if you get readable textual matter or not . I ’ve outlined a few of the more interesting file in reddish boxes — all but the first are pure text files . have ’s take a quick facial expression at each , hop-skip the first ( Archive.bom ) for now .
• 76.info : If you see a .info file in a software , you could probably learn a lot by opening it first . So what ’s in this special filing cabinet ? Here are the first few lines of the one from the 76 disk icon :
The other important line of business in this file is the DefaultLocation personal line of credit . This tells you where the file will be installed . In this case , the listed directory is /Library / Internet Plug - Ins . This makes sense for a video codec , so there ’s no useful info there . However , knowing the installation folder will be useful subsequently on .
• Description.plist : If you ca n’t find a .info Indian file , face for this file instead , as it will contain like file . Opening this Indian file , I found another copy of the “ Its a suppa puppa desc yo ” description . assume five .
• License.txt : The 76 software system includes this file , which at first glance , appears quite official :
YOU SHOULD CAREFULLY READ THE FOLLOWING TERMS AND CONDITIONS BEFORE USING THIS merchandise . IT CONTAINS SOFTWARE , THE USE OF WHICH IS LICENSED BY LICENSOR TO ITS CUSTOMERS FOR THEIR USE ONLY AS SET FORTH BELOW . IF YOU DO NOT concord TO THE TERMS AND CONDITIONS OF THIS AGREEMENT , DO NOT USE THE SOFTWARE . USING ANY PART OF THE SOFTWARE INDICATES THAT YOU ACCEPT THESE TERMS .
THE PRODUCT IS PROVIDED “ AS IS ” . THERE ARE NO WARRANTIES UNDER THIS AGREEMENT , AND LICENSOR DISCLAIMS ANY IMPLIED WARRANTY OF MERCHANTABILITY OR FITNESS FOR PARTICULAR PURPOSE . ”
So what ’s the job ? If you were to take the full correspondence , not once would you find a society name listed . Even in the quote above , it ’s always “ licensor , ” which is never fix . Contrast that with any other license understanding you ’ve ever seen , where the caller name will be mentioned at least once , but usually many time . Strike six .
• preinstall and postinstall : These are the book that are executed at the start and end of the installation appendage . They ’re the unity that actually install everything . ( In the projection screen fritter away above , you could also see preupgrade and postupgrade ; these are scripts that would run if you were doing an rise install . In this type , though , they ’re selfsame to their “ install ” counterpart . )
If you ’re not a programmer , you might think what you find here is useless . But that ’s not the case . spread the data file in a text editor , and you may discover that you’re able to actually understand some of it , or you may line up things you’re able to apply to look for the net . Consider this one objet d’art of code from preinstall :
The very first line is a unix executable namedscutil . Using Google or your favorite hunting engine , you could look upscutiland find that it does n’t seem to have anything to do with video codecs , so for me , that ’s come across seven .
As you scan the code , look for other word that can be fed to Google to find more data ; there ’s a ton of knowledge out there to be found , and even with just a few central words , you may be able to get a sense of what the program is doing . It ’s not guarantee , of course , but you ca n’t hurt anything by search .
The bom file
metre to revisit the first file in the list , the Archive.bom file cabinet . By now , at least for this app , this step would be completely optional , as I ’ve already counted up right smart too many strikes for the app to be installed . But the .bom file is a possible treasure treasure trove of information , as it contains a list of all the files the installer will install . These file may not always be named Archive.bom , but they will always end in .bom . You will have to use Terminal — very briefly — to get to the contents of this file . Here ’s the easy style to do it .
Open a Terminal window , typecd , press the Space Bar , then switch to the Finder ( do n’t press Return yet ) . In the Finder , get to the windowpane containing the installer ’s Contents folder — you may have to control - tap the installer and choose Show Package Contents if you closed this windowpane in the beginning . Now drag the Contents pamphlet into the Terminal window , and drop it .
terminus will auto - complete the path to the Contents folder ; press Return to accomplish thecdcommand . To get the cognitive content of the bom file into a usable text file , type this command :
The first one-half of the above course runs a Unix dictation that reads the bom file . The greater - than sign redirect the output to a file cabinet you specify . In this case , that file is on the Desktop , and it ’s named xyzinstaller.txt . government note : do n’t use a name with blank space in it — it just complicate matters . Keep the name short and gentle , and rename it in the Finder after if you want .
Now trade to the Finder , and enter the file you just created in a text edition editor . Here ’s what you ’d see if you did this for the 76 package :
Ignore all the numbers you see ; the other information there is the list of literal single file the installer will install . The location is what you noted before from the DefaultLocation phone line , so all of these are run low in the /Library - > Internet Plug - Ins folder . depend on the installer you ’re looking at , the selective information provide here may or may not be useful . However , if you have installed something and want to get rid of it , you could expend the entropy from the bom file to remove all traces of it .
One thing about this list that I question immediately is the naming : why is a plug - in being call with “ Mozilla ” when it ’s not necessarily wed to a pay web internet browser ? Remember , this is say to be a television playback codec , not some propagation for a particular internet browser or grade of web internet browser . It should be named something like my other video codecs — DivX , Flip4Mac , RealPlayer , etc . The last Indian file , sendreq , also gives me pause : what ’s it sending , and why ? Taken together , this is strike eight .
Optional aside: The actual installation files
So the bom filing cabinet tells you what ’s going to be installed where . But where are those actual Indian file that the bom single file refers to ? They ’re conceal inside a compressed single file within the installer — typically something like Archive.pax.gz or Archive.pax . you could copy this Indian file to another location , and then expand it ( you ca n’t thrive it in place , because you ’re using a learn - only disk image ) in the Finder — it will handle the .pax.gz and .pax formats .
When you exposit the file , you ’ll twine up with a booklet containing the files show in the bom data file . In the case of the 76 malware , there were three filing cabinet there — the Mozillaplug.plugin ( which is actually a bundle moderate the other files shown in the bom file ) , plugins.options , and sendreq . For many programs , these files will be binary code , which are n’t viewable in a schoolbook editor . But in the case of 76 , they were text files — shell scripts — so I was able to look at them in my text editor program .
Plugins.preferences is a copy of the preinstall playscript , and it ’s the code that is fulfil by the cron chore ( as described in my initial clause ) to insure that the ‘ bad ’ DNS server entropy is always in piazza . Sendreq is run only once , then deleted . It collects some basic information on your automobile ( amazingly nothing overtly scary , just your processor type and machine name ) , and then mail it to one of the forged host .
Analyzing these files is a bit more complex than analyzing the others , but the procedure is basically the same : eyeball the words , and see if it puddle some amount of sense . recover keywords and get Google to help you define what those keywords do . Look for references to matter that should n’t be associated with whatever you ’re doing . In the case of sendreq , for case , there were references to IP addresses and some ‘ socket ’ poppycock tie in with meshwork action , which lead me to enquire why a video codec involve to compile entropy about my machine and send it somewhere ?
Wrapping it all up
At this point , I would have killed this download eight times over — typically any one tap would be enough for me to do that . But I wanted to take the air through the complete appendage so you could gain some perceptivity into how a non - technical eccentric can take a looking at a confutative package prior to installing it — and using ( basically ) nothing other than a text editor in chief and the Finder .
Of naturally , the safest thing to do withanyquestionable packet is to just cast it away and see if you may find out more about it on the Net before go . But if you ’re inquisitive , the method acting I ’ve outlined here will allow you to safely examine practical software packages prior to installment . Just keep in mind that nothing is insure , it ’s possible to realistically bull almost everything I ’ve just shew , and that you could still get burn off if you proceed with an induction of questionable package .
[ Senior editor Rob Griffiths oversees theMac OS X Hints Web site . ]