Two - factor authentication ( 2FA ) is the previous matter that hundred of billion of people will likely be dragged into using for the aim of guarantee their secret information . It ’s necessary , and will be irritate to most people , despite their having seen some of the endless report of site being cracked and passwords being revealed — whether the countersign were stack away in clear text , or using an bumpkinly encoding method acting that allows crackers to well essay coarse watchword against the steal info .
make 2FA as painless as possiblewhile continue its improved surety is a challenge : most the great unwashed already have hassle managing passwords , and this add up another bed . Apple ’s approaching before a few week ago was n’t defective ; it just was n’t implemented as throroughly as it is now . However , Apple and others have kept a very large loophole to forefend breaking third - party software , which is exactly the fertile earth in which exploits grow .
Should you apply Apple ’s 2FA ? Yes , enable it immediately . Should mass who are n’t as technical as you use it ? Yes , and help them!It takes a little effort to go under up , but nearly all of the exploit is only required once . Can Apple do even more ? You play ; read on .
First, some background
Most readers of this column in all probability already know that 2FA ( also called two - stone’s throw verification ) combines two method of test one ’s valid access to a resource , like a website or an account : one method acting is conventional , and typically a password . The 2d , a item generated by a standalone strong-arm keystone , a tap using a card , a CAT scan of a biometric sensor , or a few digits generated by an app or sent as a text substance to a phone . ( There can be three or more factors , but you do n’t see these in consumer use . )
The opinion is to have an “ out - of - band ” method of create or validating identity operator : a watchword may be slip , but a confirmation ask another course , such as a forcible equipment or an algorithm seed with finicky bit that ca n’t afterward be discovered . By using a different isthmus to receive the 2nd constituent , even if a watchword is stolen , approach to the story or service stay out of reach . ( Keystroke - capturing and other malware can allow someone ’s approach to be hacked in real time during an dynamic session by capture the data point ledger entry of the code or hijacking the session ; and site vulnerability have been overwork to route around 2FA , too . )
If you ’ve used app - specific passwords with your Google account , the iCloud subroutine will seem conversant .

In possibility , one could have an extremely faint countersign , like “ 123456 , ” and trust on the 2nd factor to prevent an feat . In practice , no sensible person would recommend it , as having a firm first wall — breakable only through a site via media — is a good defense made solid by the second wall .
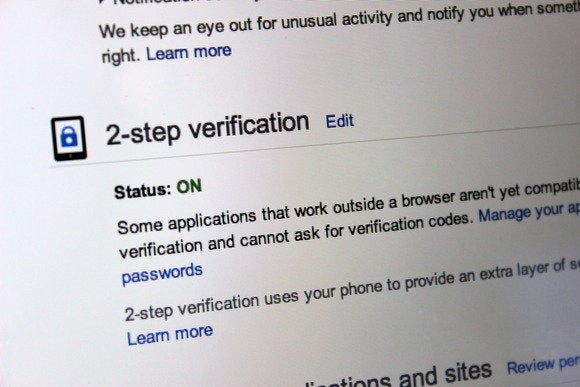
Apple was n’t early on the 2FA bandwagon , seemingly in large part because of the incumbrance it imposes on regular users who may vex about surety , but who do n’t want the friction that a second factor imposes . I ’ve used a numeral souvenir generator ateBay / PayPaland a parentage - trading site for several years , and addedGoogle ’s 2FAwhen it became available . Large companies were using smart cards and other tool for well over a X for internal resources and for validating remote access code .
Locking up iCloud
iCloud bring 2FAin March 2013 , and it has several pieces peculiar to Apple ’s ecosystem . You use the Apple ID site to enable and grapple the two - gradation verification ingredient ( explained inApple ’s FAQ ) . It requires at least one trusted gadget : something that can lam Find My iPhone or receive an SMS , with at least one of the trust gadget being MS capable . Apple provides a 14 - theatrical role convalescence key fruit as a backup . you’re able to find access to an account after lose a password or all commit - gimmick approach so long as you keep the recovery key . If you lose two of the three element ( watchword , all desire machine , and recuperation key ) , your report is locked forever .
As more Apple users rely on iCloud to sync and store their data , iCloud security will continue to be a large deal .
Until of late , 2FA was only required for specific actions , mostly in iOS . iCloud.com only required your password , and iCloud backup could be recover and unlock with forensics and cracking computer software without the usage of the second factor . After the latest security department fiasco involvingthe acquittance of private photosof famous multitude , part of which was made potential through brutal - force-out attacks against iCloud passwords , Tim Cook said they ’d batten down the hatch , andthey now have .
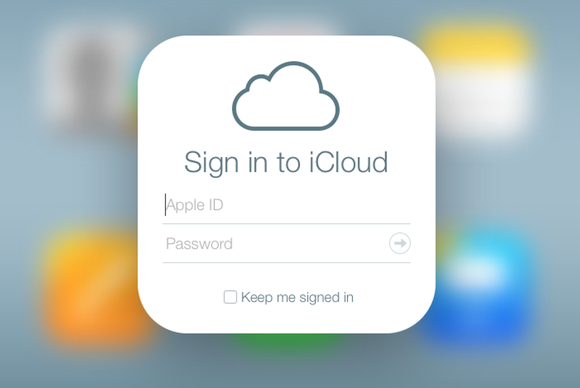
It begin with more alerting via electronic mail and organization messages about write up modification , stay with 2FA being amply implemented for iCloud.com , and mostly completed last week by requiring anapp - specific passwordfor third - company apps and services that get at iCloud for mail , contacts , and calendar items . ( Google has offer app - specific passwords since it stick in 2FA in 2010 for business customers and its broader rollout to all drug user in early 2011 . )
A new password for each app
These sort of passwords have nice properties and one huge drawback . Because they ca n’t be chosen but only generate , Apple creates ones that are long and inviolable , which makes them fundamentally impossible to crack through brute force open all currently screw technique . They ca n’t be recovered : once produce , and the Done clitoris is pressed , Apple does n’t keep back any noesis of the original nor provide a direction to retrieve it — only the one - way encrypted form is retain .
The management creature at the Apple ID land site on the Password and Security’sView Historysection let you revoke these passwords , too : one at a time or all at once . And whenever the independent bill countersign is transfer , all the app - specific ones die a sudden death , too .
It ’s authoritative to apply two - factor assay-mark wherever you could , particularly on situation and servies that could draw into your iCloud explanation .
They do bypass the two - factor benefit , however , and that ’s a headache , e-mail most of all . Apple ’s 2FA forestall access to its own history information for confirming a password change . But with any single - factor account you had elsewhere for which the registered email is your iCloud one , a third party who gain access to an app - specific password would be able to reset parole at other service .
Now , the gracious part with most of this is that you are n’t tease that often , if ever , after going through the bickering of setting it up , which is what cause it potential for you to help others ( family , friend , confrere , and more ) , as you wo n’t have an on-going burden of support . Setting up trusted devices takes a few mo . Generating necessary app - specific parole , a few more , depending on how many dissimilar e-mail client , calendar apps , and contact manager you use that lecture to iCloud .
Most people tend to habituate a exclusive computer or exercise set of computers , and Apple will let you apply 2FA the first clock time you lumber into iCloud.com on a make web browser , and then just a watchword when a seance times out thereafter .
Two - element authentication does n’t solve security . There are many points of entry for exploitation , and more being discovered ( and piece ) all the time . What it does is prevent a butter knife from picking the whorl on your front threshold — and usually preventing a sledgehammer from ping it down as well .