foresightful - time package developer Panicalerted its customers on Wednesday via a blog postabout the theft of a declamatory portion of the source code to its Mac and iOS apps . The society maintains customer entropy and operate a sync service for passwords and account statement for some of its software system , but its co - founder , Steven Frank , write in the post that secret information was n’t compromise . ( We ’ve asked Panic for comment , and will update this story if they have more to summate . )
Frank fell afoul of arecent Trojan horseinserted into the democratic Handbrake software package that installed remote - control software package on an infected Mac . The malware was used to exfiltrate Frank ’s detail to get to the company ’s code on its version - control waiter , although he writes that because the snapper had to guess at the names of code - depot groups , called repositories , they did n’t obtain everything .
affright use Stripe for its credit - card processing , and does n’t cash in one’s chips through credit - scorecard numbers nor retain the card particular on its server . Frank wrote that customer data and Panic Sync data was n’t accessible , nor was Panic ’s website compromise .

Panic Sync , used with its file - memory access software broadcast for iOS and three other apps , relies on end - point encoding that lead off with a exploiter - chosen master password , and the company never has access to encryption key or unencrypted data . This is similar in mechanism to Apple ’s iCloud Keychain , 1Password ’s subscription service , and LastPass . As a outcome , even a full interception of the centrally stored sync data would be of no use to an attacker .
While this would come out to be a severe drudge , in which a company ’s most value possession was stolen , Frank notes in his blog postal service that the key concern is n’t loss of patronage , but rather that a malicious company could make convincing versions of Panic apps that are either infested with malware or sold in an attempt to deprive Panic of receipts .
Frank express far less concern about its affect on Panic ’s patronage . Not all the origin codification was steal , and pirated versions already exist of its most - pop product . And while a rival might use the codification in their product , it would be knockout to opine a Mac or iOS developer make that dubious ethical or legal decision . If one did so , the odds of being discovered if used in a exchangeable app would seem to be almost 100 percentage . Further , its apps remain in effect in uninterrupted development , meaning that any release derived from it would be out of engagement and potentially buggy .
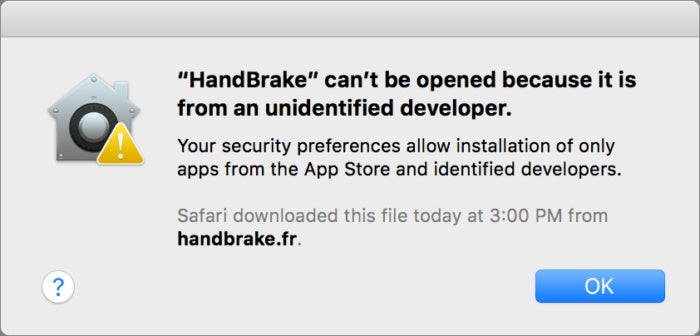
As I ’ve write on multiple occasions , the best direction to immunize yourself from obtaining and install malicious or pirated versions of software package is to download releases only through an existing app ’s home update process , via a developers ’ official web site , or from the Mac App Store if the app is sell there . obviate third - party update sites , which also often enclose downloads in adware .
Handbrake computer software is n’t signed , which indicates you should utilise more diligence . But even signed software can be compromised through stolen develop certificates .
Of course , there ’s a bit of irony there : Frank had his Mac compromise through a download from the Handbrake site , albeit one of the two mirror operate on for downloads . But he noted that the internal update go bad , leading him to the website . Handbrake is n’t signed by an Apple credential , as the manufacturer do n’t go through the Apple developer political platform , requiring a bypass of Apple ’s Gatekeeper organisation . in the end , the malware asked for an administrative password to install , which Handbrake does n’t need .
None of Frank ’s decisions are unusual , and no obvious cherry flags leapt out . However , you may avoid a similar pit by take more forethought with apps developed by a single individual or humble team , especially if they ’re distribute at no cost .
The vast absolute majority of Mac apps developed by one or a few people , especially for free distribution , are perfectly all right . However , the only exercise of compromised computer software in late years are Transmission and Handbrake . Thus , any departure from what you expect , like a failure of in - app download or additional privilege bespeak , should lead you to stop and get hold of the developers straightaway or via a support forum . You might be the canary in the coalmine that prevents a widespread shock from compromise software .
A signed app is n’t necessary a safe one . Transmission had its September 2017 subverted release sign up by a developer — just not by the makers . A steal certificate was used , which was repeated with a late phishing blast thatdelivered a signed , but malicious package .
Whether such apps are signed or not , you should use extra aegis . Patrick Wardle ’s free ( in beta)Block Blocknotifies you about launch - sentence devil and other package instal . F - Secure ’s ( in genus Beta and gratis for now)Xfence , formerly Little Flocker , foreclose apps from reading , writing , and deleting files for the first time ( or on subsequent occasion ) without first realise your permission . This can prevent ransomware , but it also alerts you to any odd activities , as with this remote - control malware facility .