FREAK is last week ’s worry , but installing untrusted lotion is a recurrent vexation . It ’s a two - fer ( or two - fear ) in this column , about security department issues new and old .
Super FREAKy
Apple expel update this week for a security exposure love as FREAK . FREAK allowed a malicious party to force a weak encryption communications protocol to be used between about one - third of web server with security system certification and many secure web clients and commonly used software package program library . That weak communications protocol could be break up inexpensively and relatively quickly to reveal the message of a session between a web browser app and web server . ( you may read the full point about the flack in Jeremy Kirk ’s news show written report . )
Apple confirmed on March 3 that it would relinquish update the succeed week , which it did . This is better communication than usual , couple a more late formula . In the past , the society often remained mom about when surety fix would come , even when they were quite stark . The frankness is welcome .
Get those updates .

The updates are for OS X 10.8 ( Mountain Lion ) , 10.9 ( Mavericks ) , and 10.10 ( Yosemite ) ; Xcode 2 ; iOS 8 ( included in 8.2 ) ; and 3rd contemporaries and after Apple TVs . This seems like a relatively little windowpane of update , given that the fault is present in operating scheme of all variety dating back a decennium .
But the location is asymmetrical : it can be blocked either or both in clients and servers . Web internet site immediately start relatively minor reconfigurations that foreclose the flaw from being exercise , regardless of what inviolable software attempting to plug in attempt to do . Sites that have bothered to install security certificates ( or require them for their business ) are likely to update their options if they fall into the class of bear on servers .
FREAK is one of a family of irritate feat that there ’s nothing you’re able to do about on your own , nor have done as a preventative , to keep yourself safe . However , engaging the exploit would expect a party with horrendous intent to enter themselves as a “ man in the center ” ( MitM ) . For all users , the likelihood of interception is low ; for special user , who might be target by foe , criminal , or a administration agency , the odds would be moderate to quite gamy — if this feat were bed and in employment as a tool of interception or theft .

As it stands , those with OS X 10.7 and in the first place or iOS 7 and earliest should n’t fret , they iOS users may be feeling like . The holes have been closed so rapidly that this is n’t likely to be a useful instrument in the kit of those bent on interception .
Don’t take any wooden apps
There ’s news that malicious installers for Mac software have started to pasture up again . This is n’t the first time this has happened , but it ’s often surprising to OS X users that there ’s any reason to vex because of Apple ’s generally great approach to software installation that prevents malware from gain a travelling bag without user interposition . But even if you would n’t be suckered in , you might check friends ’ and relatives ’ configurations and understanding to ensure they ’re safe .
The installer cozenage involve software , often legitimate and desirable , that is twine in a package that makes it seem as if one needs to also install other , unrelated computer software . Some of it is pure malware , but all of it highjack some scene of your experience , such as adding web browser extensions , redirecting your nonpayment search railway locomotive , or generating popups . The intention is to fascinate your attention to add chink that the installation package Lord is pay for or to put one over you into purchase .
For function of software hygiene , I urge never installing OS X software downloaded from anywhere but the Mac App Store or the developer ’s site , unless it ’s via a tie render by the developer to an substitute download . With some candid - source , complimentary , or alternate distribution role model software , you may necessitate to download elsewhere , but the project ’s home will almost always manoeuvre you there . ( This assumes any given developer is n’t unethical , which is intimately always true . )
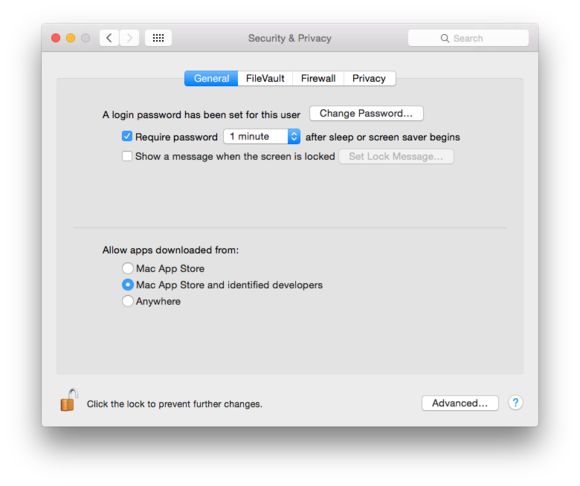
organisation Preferences > Security & Privacy is your first crinkle of defense .
The next level of safety is in the Security & Privacy preference pane ( in Yosemite ) . In the General tab , the Allow Apps Downloaded From set of option let you mold the layer of default installation jeopardy . you’re able to opt for Mac App Store only , the storage plus Identified Developers , or Anywhere — if you dare .
For less - sophisticated Mac users you recognise or help with their calculation needs , the Mac App Store might be the best pick . If they do n’t routinely or perhaps ever set up third - political party software or always require your or someone else ’s assist , it ’s a dear way to preclude a uncollectible , inadvertent outcome .
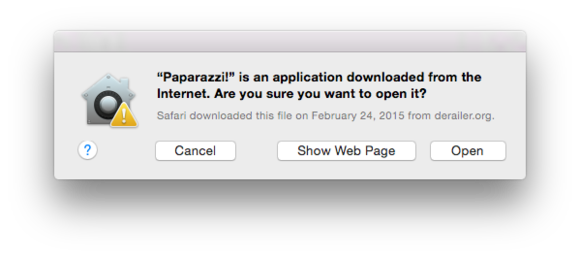
With the heart scene take above , you ’ll still get a warning about software system you download from the Internet . ( Mac App Store computer software is vetted to be safe . )
The in-between choice , Mac App Store plus Identified Developers , only allows the straightforward instalment of computer software that ’s been sign by a digital certificate issued by Apple to a specific developer . The installer scam software may , in fact , come from party that paid the $ 99 - a - year fee to be part of Apple ’s OS cristal developer program , and are misuse their membership or stretch it to the extreme limit .
This is why avoiding download land site is a good scheme to begin with , rather than rely on this security setting in OS X. Apple can rescind developer certificate easy enough and agitate out other curative , but it ’s effective to not fall into a site in which that refuge is what you swear on .
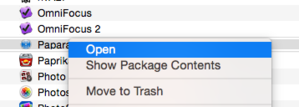
usurp you hope the developer , you could still instal unsigned computer software by right - clicking it on first launching and selecting Open .
I always advise against the Anywhere setting , because then you allow down your guard . With the middle setting , you’re able to still install unsigned software system . Find the software itself , right - click it , and select Open , and you ’re prompted to confirm that you need to launch it .