To get to the bottom of how serious a menace a piece of malware really is , sometimes you have to take drastic stairs — like by choice infecting your own Mac to gauge the scope of likely scathe . That ’s what I did with the Leap - A malware that emerged Thursday , and I ’ve learned that the program — while cunning — is not about as malicious as it could have been .
First some ground : as I reported in the Leap - A FAQ , Leap - A ( or Oompa Loompa , as it ’s also acknowledge ) is a potentially malicious programme disguised as an image file . lucubrate the squeeze archive and bivalent - click the resulting file cabinet , and Leap - A will jump into action , installing itself on your system . The launched malware reportedly does two things : send a version of itself to everyone on your iChat buddy list and infect programs written in the Cocoa maturation environment . Once infected , those programs wo n’t be able to launch .
In the course of spell the FAQ , I felt that I need to have Leap - A on my organization , so that I could understand what it did once it was installed , and to understand how to recover from it . I also knew I could n’t do this alone , as I ’d need to have someone to test the iChat portion of the code with . I call on tenacious - timeMacworldcontributorKirk McElhearn , who set up a test machine in his place as well . What follows is the result of both of our efforts ( so even though you may study “ I , ” this was really a team effort , as noted by the byline above . )
frame-up
The first matter I did was set up my tryout machine , my handy PowerBook . I installed a fresh version of OS X 10.4 on a partition on a FireWire parkway , updated it to 10.4.5 , and then put a copy of Leap - A on the FireWire drive . I then bring up from the FireWire driveway and then unmounted the internal heavy drive ( for rubber ’s sake ) . I also incapacitate AirPort and disconnect the Ethernet cable . I now had an effectively isolated motorcar , quick to suffer the anger of Leap - A.
Pulling the Trigger
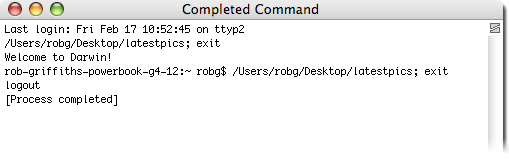
With a slimly unquiet finger , I double - penetrate the .tgz file , observe it expand , then doubly - clicked the “ JPEG image ” to launch the malware . For all of you who are rummy , here ’s on the button what happened . A Terminal windowpane appears , with the results of a script ’s execution :
At this point , the malware is now installed on the machine . If you have your InputManagers folder owned by solution , however , you ’ll instead see a “ Permission Denied ” mistake content in that window . ( Note that the bit that infect software will still be set up . ) The other affair that ’s happened , which you wo n’t see , is that your / tmpdirectory now admit a copy of the .tgz archive , quick for distribution via iChat ( more on that afterward ) .
Examining the impact
So there I was , ready to see the baron of Leap - A. Since the automobile was n’t on the net as of yet , I think I ’d let it junk a few apps for me . So I launch and quit various Apple - provided Cocoa apps ( since that ’s what came install on the machine)—Safari , Mail , Address Book , iCal , Terminal , Console , and so forth . All of them spread out fine the first time . And the 2nd . And the third . And the fourth . It seemed this share of the malware was inefficient , at least on my auto . After a while , I give up on that front , and decided to prove the iChat portion of the program .
Kirk and I both arrange up new AIM identities to use in our iChat tryout . I re - enabled AirPort , plunge iChat , and signed in with my ID from my now - infect PowerBook . When Kirk logged in , I add his ID to my buddy list , and waited for the fireworks . Nothing happened . We both tried various combinations of renounce and relaunching iChat , and transfer other files to each other , but we could n’t repeat Leap - A ’s report behavior .
Kirk then infect his test simple machine as well , but still nothing — no files were being send in either direction without one of us start a file carry-over in the common manner . ( He also could n’t make the malware destroy any of his apps ) . After a practiced time of day or more of this , we give up on this circumstances of the malware ’s alleged actions as well .
By now , I was several hours into this cognitive operation , and beginning to think this whole thing was just a bad antic . All I ’d managed to do so far was have a few files created on my PowerBook . But I could n’t get Leap - A to vote out any Cocoa apps , nor could Kirk and I get the malware to send itself out via iChat .
Friday morn , I was still bothered by my PowerBook ’s apparent indomitability to Leap - A , so I connected with Kirk again via iChat ( using our “ healthy ” systems ) . But this meter , Kirk was in contact with someone from Intego , makers of theVirusBarrier X4anti - virus computer software . Through a very protracted debugging process ( yes , we were spend time debugging a piece of malware ! ) , we think we ’ve finally figured out exactly how both piece of Leap - A work , as well as how to best recover from an infection . Credit for most of the chase goes to Kirk and the folks at Intego ; I was only a guinea pig and sound board for much of the process .
get off via iChat
It turns out that Leap - A will only charge itself out via iChat under averyspecific lot of circumstances :
So it seems the “ iChat infection ” aspect of the Leap - A malware has been greatly exaggerate — unless you apply Bonjour iChat , you ’ll never see it come on your machine in this manner .
Infecting ( and Breaking ) Cocoa Applications
This was the surface area where both Kirk and I were really confused . Everything we ’d register point that our Cocoa applications should be quickly infected by Leap - A , and at that dot , they would then break working . Yet as we kept testing , everything proceed to work . I even tried something extremist ( which I wouldneverrecommend on any production machine ) , and made the entire Applications pamphlet interpret and write approachable to all . Even then , I could establish , quit , and relaunch Cocoa apps at will . The only sign of the zodiac of Leap - A was a one - line submission in theconsole.logfile each time I launched a Cocoa app :
For whatever reasonableness , the InputManager was go wrong to load when I open up a Cocoa app . Kirk was seeing the same thing on his auto , and after a sight of brainstorming ( and a fair bit of cussing ) , we found out why it was n’t work . It turns out that Leap - A willonlymodify Cocoa applications that are owned by your user , and not the organisation . Since both Kirk and I were testing with Apple - provided apps , all of which are system - owned , we could n’t corrupt any of those apps . Safari , iChat , Mail , and the like are all seemingly secure from the burden of Leap - A.
After this breakthrough , we started experiment , and figured out how this matter operate with a new plague . Say it ’s a typical workday , and you ’ve launchedOmniWeb , surfed the entanglement , and find some cool picture of OS X 10.5 . You download the archive , inflate it , then doubly - click the JPEG . You ’re a bit surprised when the Terminal windowpane open up , and no photograph show up . But it ’s a engaged day , so you do n’t think much of it . You have , of form , now set up the malware on your automobile . You quit OmniWeb , go about some other work , then launch OmniWeb a piece later in the Clarence Day . At this level , Leap - A strike , and OmniWeb is now infected . The rationality OmniWeb becomes septic , and not Safari , is that OmniWeb is set up via a retarding force - and - driblet . When you install in this manner , your user is the owner of the programme , not the scheme . Hence , it was susceptible to Leap - A.
AsAndrew Welch take down Thursday , when you attempt to set in motion the fresh - infected app , an apparent glitch ( or is it a characteristic ? ) in the code prevents it from launching . But , behind the picture , a draw just happened :
Now , the practiced news in all of this is the bug ( lineament ? ) that breaks the infected diligence . Since , in this example , OmniWeb is no longer working , you ’ll be very unlikely to launch it again after that first “ stagnant ” double - detent . Instead , you ’ll probably just go download a clean version , which wo n’t be infected . If the bug ( feature of speech ? ) did n’t live , then you ’d never cognise that each launching of OmniWeb was also searching for other uninfected apps to taint , and your machine would become much more badly infect over time . That ’s why I recall this is a bug , not a feature . ( It ’s only a feature article if the author ’s spirit is to only erupt all your installed lotion . )
The above physical process will echo each time you attempt to launch an septic software . finally , if you let this go on long enough , you ’d find out that all of the Cocoa software that are owned by your exploiter will no longer work . Hopefully , though , the non - functional applications would indicate to you that there was a problem . What do you do then ?
Recovering from Leap - A
For this particular piece of malware , I call up the simple solution is to transfer the computer virus and replace any damaged applications . You could choose to reinstall OS X , but since the malware does n’t impact any system - possess software , and your datum file are safe , this seems like overkill to me . So here ’s a step - by - measure guide to removing Leap - A from your arrangement :
This last step is where things get a bit tricky . If you attempt to spread a wiped out practical program , you ’ll reinstall the malware , and possibly taint a few more applications . Hopefully you may only remember which programs do n’t work . But if you ’re not certain , you could try these mastery in Terminal :
The first bid moves into the Applications directory ; the second instruction checks the modification times on executables within program program package in that brochure . ( If you store other programs elsewhere , cdto that directory , too , and then iterate the second command . ) Typically , the qualifying time on an practicable will not usually alter after you install it ( unless you run an updater for it , which you would hopefully remember ) .
Since Leap - A does make changes to the viable , we can look for changes to the feasible ’s timestamp to identify affected software . The last spot of the command,-cmin 60 , tellsfindto show app change in the last 60 minutes . Modify that time period as necessary for your organization ; hopefully if you were to get infected , you would detect very quickly , so you could use 5 or 10 , not 60 . If you do n’t recall running an update to something in the returned list , delete the political program and reinstall it from source .
Conclusion
Leap - A is sure a tricky piece of code . Due to a combining of bugs in its code and decisions made by the author , however , it ’s not intimately as malicious as it could have been . It really does seem like a “ test copy of concept , ” designed to show that such things are possible , without doing a great amount of harm . It should , however , serve as a effective wake - up call for all of us to closely examine those things we download prior to making the double - click decision .