You might have see about WannaCry , ransomware that crippled NHS computers back in May 2017 , and the Petya randsomware attack that hail at the end of June 2017 . It ’s been a while since these high - profile cases that were only a danger to personal computer users , but you might be wondering if , as a Mac drug user , you should be doing anything to protect yourself from such threats , and how to fix thing if you get hit by ransomware .
Here ’s everything you need to know about detecting , avoiding and removing ransomware on Macs .
What is Ransomware?
Before we expect at the pillow slip of Ransomware on the Mac , we ’ll explain what Ransomware actually is . It is a type of malware flack where your file cabinet are encrypted against your wish and a ransom money need tells you to pay a fee if you want to get the file decipher again .
As reference above , Ransomware is a business for Windows substance abuser , with WannaCry and Petya being well - known instance on that platform , but is it something to occupy about if you utilise a Mac ?
Well , if you use Windows on a Mac you should obviously be as cautious as you would be if you were using Windows on a personal computer , but if you use macOS Apple has a bit of safety measures work up in that should protect you , right ?

Unfortunately even Macs have been affected by Ransomware attacks , although these are very rare , as you will see if you show on .
This is one of several in - depth Macworld articles dealing with Mac security system . If you ’re looking for AV buying advice , read our roundup of theBest Mac antivirusandDo Macs get viruses ? ; general advice can be found in ourMac security steer ; and those who think they have been strike by a virus should tryHow to off Mac viruses . We also have a fulllist of Mac viruses here .
Can Macs get ransomware?
Can Macs be infected with ransomware ? Has there ever been a case of Mac ransomware ?
The answer is yes , but it ’s a very rarified occurance . There have been a fistful of Mac ransomware illustration identified by certificate investigator to day of the month , but not one has leave to serious outbreaks and few if any Macs have been pretend . However , the leaning make interesting version to learn how a future ransomware eruption might diffuse and how it might operate .
ThiefQuest / EvilQuest (June/July 2020)
Malwarebyteshighlighted that malicious codification was distribute in pirate copies of Little Snitch and other Mac programs on a Russian downpour meeting place Rutracker .
The program attempt to install itself in several plaza in the system hides behind name like “ com.apple.questd ” and “ CrashReporter ” . If you install it on your computer it will begin encrypting data file before demo you a blackmail substance asking for $ 50 bitcoin to decipher the files . say more about it here : Mac ransomware could encrypt your Mac .
It ’s guess that the ransomware element of this malware might be only part of its aim – the malware seems to search for certain file types before charge them to a central host before any Indian file are write in code .

FileCoder / Filezip / Patcher (February 2017)
surety researchers find and identifyFilezipransomware masquerade as “ patcher ” apps that can be downloaded from plagiarisation sites . Patcher apps are design to illegally alter popular commercial software like Adobe Photoshop or Microsoft Office so they can be used without purchase and/or a permission code .
When the user attempts to use the patcher app , Filezip instead encrypts the substance abuser ’s files and then places a “ README!.txt ” , “ DECRYPT.txt ” or “ HOW_TO_DECRYPT.txt ” file cabinet in each folder listing the ransom money demands ( 0.25 BitCoin ; around £ 335 at the time of writing in May 2017 ) . Notably , like many Windows - based examples of ransomware , Filezip is unable to actually decipher any single file , so pay the ransom is pointless .
KeRanger (March 2016)
Security researcher find and identifyKeRangerransomware within an authorised update for the Transmission BitTorrent client . The first real example of Mac ransomware , this clock time the ransomware creators have clearly made an effort to create a unfeigned threat .
KeRanger is signed with an authorised security certification , so is n’t blocked by the macOS Gatekeeper security system , for good example . KeRanger encrypts file and then leaves a README_FOR_DECRYPT.txt file in the directory , in which the ransom demand is made ( one BitCoin ; around £ 1,338.62 at the time of composition in May 2017 ) .
However , thanks to fast legal action by the researchers and also Apple , who immediately repeal the surety certification , KeRanger is halted before it becomes a serious threat . If both agencies had n’t been quite so flying off the mark , however , it could ’ve been a very different report .

Gopher (September 2015) and Mabouia (November 2015)
Two security investigator , working independently , separately createGopherandMabouia , two examples of ransomware specifically targeted at Macs . However , both are only proof - of - concept demonstrations , mean to show that fully fledge ransomware on the Mac is exclusively potential .
Aside from copies share with security department investigator for them to learn from , neither ever leave the investigator ’ computers , so can not spread .
FileCoder (June 2014)
Security researchers found and identifiedFileCodervia theVirus Totalvirus - scanning site , although by that point FileCoder was already onetime , having been first detected by the land site ’s malware scanner two years originally .
Specifically targeting OS X / macOS , FileCoder is unfinished and not a threat , in that it does n’t in reality encrypt the user ’s data . It does exhibit an app window demanding a ransom money of € 30 ( rather cheekily , this is discounted to € 20 if a credit add-in is used instead of PayPal or Western Union ) .
It ’s not known where FileCoder originated , or how it was intended to spread .

FBI scam (July 2013)
For over a decade , website - based ransomware has attempted to extort money from fleeceable Windows user by “ locking ” the vane internet browser to a purported law enforcement website . This was always bare smoke and mirrors , however , and could be get the better of easily .
But in July 2013 security investigator chance on asimilar scamspecifically aim the Mac ’s Safari internet browser . The user was operate to a fake “ FBI ” webpage via a dialog corner that would n’t let them leave the web site , and a $ 300 “ fine ” was demanded to unlock the arrangement .
throw in the towel the web browser app was made unimaginable . If the exploiter strength - quit Safari , the ransomware page simply reload itself next time Safari started .

Apple has since fix Safari on both Mac and iPhone / iPad so that it ’s less easy for browser app - based ransomware like this to operate . However , you might still bump less virulent examples .
Can Macs get WannaCry?
Put simply , no . WannaCry choose vantage of a bug in Microsoft Windows ’ electronic web file communion organization , a applied science called SMB . Once WannaCry gets onto a exclusive computer on the connection – normally because an person open a rogue e-mail attachment – it then uses a hemipteron in SMB to inject itself into all other data processor on the connection that have n’t been piece .
Macs also use SMB as the nonremittal electronic web file sharing engineering , so you might initially think Macs could be affected too . However , Apple uses its own bespoke implementation of SMB . While this is full compatible with Microsoft ’s interlingual rendition , it does n’t suffer from the same bugs or security holes , so is n’t affected by WannaCry – or at least not in WannaCry ’s current reflexion .
The iPhone , iPad , Apple TV and even the Apple Watch do n’t use SMB file sharing , so are n’t even theoretically at risk from WannaCry .
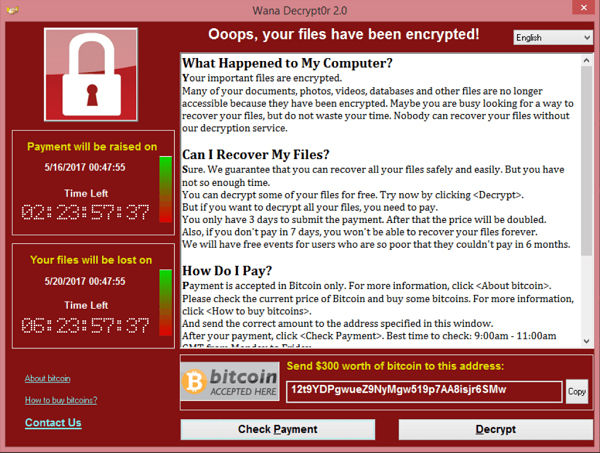
Can Macs get Petya?
Petya is another Ransomware attack , similar to WannaCry , that struck data processor in Europe and the US at the end of June 2017 .
Petya hit some big firms , and like the early WannaCry ransomware attack that affected the NHS in the UK , it spread quickly to Windows electronic computer on the same mesh .
computing machine are infect due to a vulnerability in Windows for which Microsoft has relinquish a dapple .

Most of the antivirus companies have update their software package to protect against Petya .
The Petya ransomware demand that $ 300 in Bitcoins be paid as the ransom in ordination to find access to the computer . However , the perpetrators are thought to be amateur as the ransom money note gives the same Bitcoin destination for every victim and only one email savoir-faire is provided for correspondence – which has of course already been shut out down .
The tone-beginning may have been point at the Ukrainian government rather than as a means to make money .

How to protect a Mac from ransomware
Although at the fourth dimension of committal to writing there has n’t been a serious ransomware eruption on the Mac ( or any Apple hardware ) , security department researchers reckon it ’s a real possibility .
Speaking on CNBC ’s ‘ Squawk Box ’ programme in the wake of the famous WannaCry ransomware onrush , Aleksandr Yampolskiy , CEO of SecurityScorecard , insistedthat Apple users are vulnerable to WannaCry - case attack , even if that specific effect strike Windows organisation only .
“ It pass off that this attack is targeting the Windows computers , ” he say . “ But Apple is utterly vulnerable to similar types of onrush . ”
So , have ’s hypothetically assume you ’ve been infect . What should you do ?
Step 1: Don’t panic
Take your time and avoid kneejerk reactions .
Step 2: Clean up
utilize a malware scanner like the freeBitdefender Virus Scannerto search for the ransomware and polish off it .
It ’s unlikely you ’ll be the only person affected by the ransomware so keep an eye on site like Macworld to study more about the nature of the ransomware infection . You ’ll very likely find specific command on how to strip up the contagion , if a computer virus scanner is n’t capable to do so .
You might discover that a security investigator has found a way to decrypt your Indian file for barren , something that happened with the most late example from the smattering of ransomware contagion that have been identified on a Mac .
Step 3: Don’t pay
As you ’ll see afterwards when we examine the fistful of live ransomware eruption move the Mac , there ’s a good fortune paying up wo n’t actually recover your file !
Step 4: Unplug and disconnect storage
The one example of effective ransomware seen on a Mac so far – KeRanger – also seek to encrypt Time Machine backups , to seek to make it impossible for the substance abuser to just restore file from a backup .
Therefore , upon hear your Mac has been infect by ransomware you should minimize the possibility of backups becoming inscribe too by immediately unplugging any removable storage like outside hard disks , and disconnect from any internet portion by clicking the eject icon alongside their submission in the sidebar of Finder .
Step 5: Install the RansomWhere? app
Consider installing theRansomWhere ? app . This free app runs in the background and watches for any activity that resembles the rampant encrypting of files , such as that which takes place during a ransomware attack . It then halts the operation and tells you what ’s hap . Okay , so some of your files may terminate up being encrypted , but hopefully not very many .
As with many example of ransomware and malware , WannaCry initially infect computer net via a phishing attack . Never open an email attachment you were n’t expecting , even if it appear to come from somebody you know , and no matter how important , interesting or opprobrious it appear to be .
Sept 7: Don’t use dodgy software
The most recent Mac ransomware seek to spread via “ cracked ” or patcher apps plan to countenance you habituate commercial-grade software system for destitute . Therefore , deflect all chancy software like this .
Step 8: Always ensure your system and apps are updated
On a Mac you may configure automatic update by start the System Preferences app , which you ’ll receive in the Applications list of Finder , and selecting the App Store icon . Then put a check mark alongside Automatically Check for Updates , and putting a check in all the box directly beneath this heading .
Step 9: Install only from official websites
If you suddenly see a pop - up say one of your web browser app plugins is out of date , for example , then be sure only to update from the prescribed web page for that plugin – such asAdobe ’s websiteif it ’s the Flash plugin . Never trust the link bring home the bacon in a pop - up windowpane ! Hackers make frequent exercise of such pop - ups and fake websites to spread ransomware and other malware .
Step 10: Back up frequently, and disconnect
If you have a backup of your files then it matters less if ransomware tap because you’re able to only regenerate . However , the KeRanger ransomware outbreak attempt to also encrypt Time Machine backup man , so you might choose to use a third - party app likeCarbon Copy Clonerinstead to backup your files . study more : How to back up a mack
Just backing up your Mac is n’t enough though . To be really good you should also disconnect your backup drive after the Mac has back up , that way the drive ca n’t be encrypted in an tone-beginning .
How do I protect my iPhone or iPad from ransomware?
iOS devices like iPhones and iPads were built from the earth - up to be much more inviolable than Macs , and on-key ransomware via some kind of malware transmission would be extremely difficult to pull - off . There sure enough have n’t been any examples so far , or at least on iOS machine that have n’t been jailbroken .
However , iPhones , iPads and even Macs are capable toiCloud highjacking , a type of ransom onslaught whereby a hack reuses passwords discovered through one of the manylarge - scale security measure breachesin guild to log into and take command of a user ’s iCloud account . They then change the password and use the Find my iPhone service to remotely lock the iOS twist or Mac , send the user demands for ransom money in parliamentary law to restore mastery .
Often they endanger to remote wipe the equipment or Mac in addition to this . The first such attack of this nature was the Oleg Pliss attack back in 2014 .
iCloud highjacking is easily queer bysetting up two - factor assay-mark , and you should do so now !
However , no matter of whether an actual ransomware transmission is possible , it certainly makes horse sense to secure you keep your iPhone or iPad to the full update ( readHow to update Io on iPhone or iPad ) so as to have the best possible protection against any potential menace . When a new iOS update becomes useable a notification will appear alongside the preferences app , and you ’ll be able to update by opening preferences then tap General > Software Update . ( observe that there ’s no way to configure automatic system updates on iOS . )
Any app claiming to provide antivirus scan for iOS machine is likely to be doubtful at best because all iOS apps are sandboxed , so are ineffective to scan the system or other apps for malware .
Should I run an anti-virus app all the time?
It might storm you but Macs already have antimalware built in , good manners of Apple .
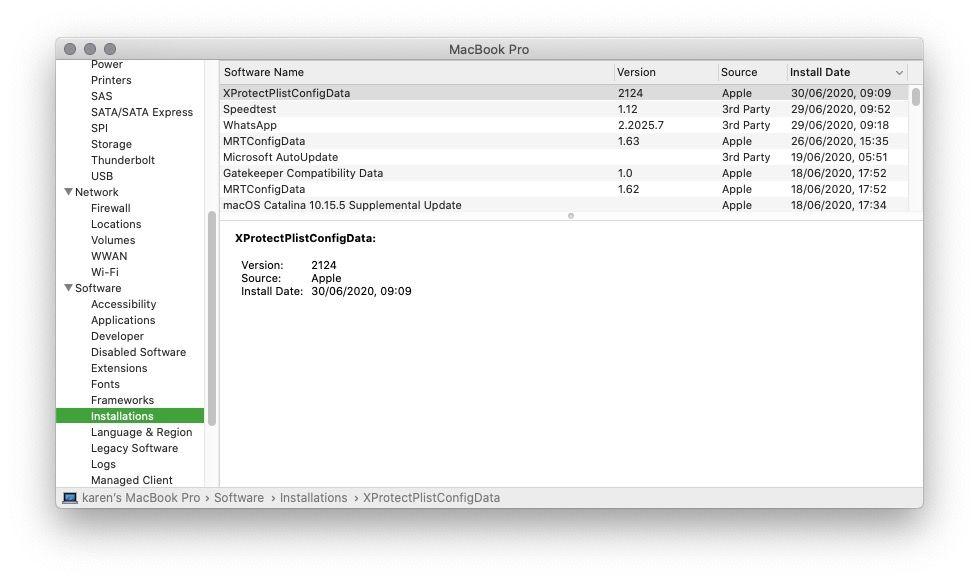
XProtect runs invisibly in the background and scans any files you download as part of the standard file quarantining cognitive process . XProtect is updated regularly by Apple with new malware definitions and you’re able to see the frequency of updates by conform to these footstep :
XProtect was how Apple was able-bodied to overcome KeRanger , perhaps the most serious Mac - based ransomware terror so far , before it had a chance to become autochthonal . to boot , the most late Mac ransomware , Filezip , has been add to XProtect too .
Combined with other built - in safeguards such as file cabinet quarantining and hall porter – both of which stop the user blithely running apps or opening docs they download from unusual websites – the Mac is well guarded against ransomware than you might think .
However , there ’s surely no harm in now and again run for an on - demand computer virus electronic scanner such as Bitdefender Virus Scanner , even if this may well find many fictitious positive degree in the variant of Windows virus in things like post attachments . Windows virus are harmless for Mac users . Read about thebest Mac antivirus software program here .