We already know thatiOS 17.4will be a game - changing update for the iPhone , with support for alternative app stores and payments in the EU , a handful of new emoji , and virtual numbers for Apple Cash cards , but Apple has one more feature in store when it launch sometime over the next few weeks . In a post on itsSecurity Research blog , Apple has outlined a new Department of State - of - the - art security upgrade for iMessage that “ has the strongest security properties of any at - scale electronic messaging communications protocol in the universe . ”
It ’s all very technical , but Apple will be deploy post - quantum cryptography Level 3 ( PQ3 ) , which “ is used to secure both the initial cardinal establishment and the ongoing message substitution , with the ability to rapidly and automatically restore the cryptographic security of a conversation even if a given key becomes compromised . ” That means a drudge would demand to crack two symmetric keys that go beyond any of the available methods used in even the most highly advanced attack .
orchard apple tree

Apple note that Signal was the first large - scale electronic messaging service to use post - quantum cryptography with the late accession of PQXDH support , which elevate the app ’s security from Level 1 to Level 2 . However , Apple tell iMessage ’s new PQ3 protocol takes it a step further Here ’s how Apple describes the protocol in action :
When Alice ’s twist instantiates a young session with Bob ’s gimmick , her machine query the IDS server for the cardinal bundle associated with Bob ’s machine . The subset of the primal megabucks that carry the gimmick ’s authentication key and versioning information is validated using Contact Key Verification . The equipment then validates the signature cross the encoding samara and timestamps , which attests that the paint are valid and have not run out .
Alice ’s twist can then use the two public encoding key out to partake in two symmetrical keys with Bob . The first symmetric key is computed through an ECDH key rally that combines an ephemeral encryption samara from Alice with Bob ’s record P-256 public headstone . The 2nd symmetrical key is incur from a Kyber key encapsulation with Bob ’s post - quantum public keystone .
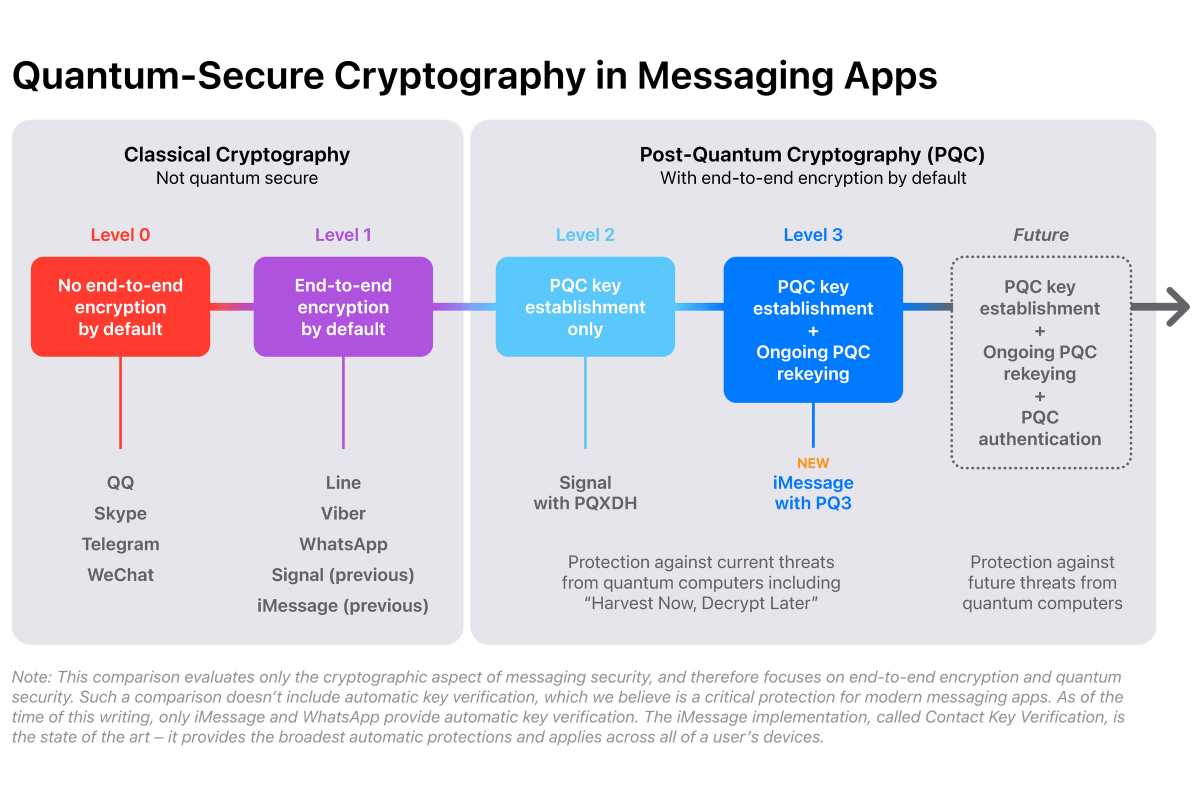
This combination ensures that the initial session state can not be deduct without knowing both of the shared mystery , intend an assaulter would postulate to break up both algorithms to recover the leave secret , thus satisfying our intercrossed protection requirement .
iMessage has been used in high - level zero - flick government attacks , most notablyIsraeli NSO Group ’s spy software package Pegasus . Apple says the young organisation is essential for safeguarding against known and unknown succeeding attempt and will protect against agents who have already collected encrypted data point for future decryption .
Apple says the new communications protocol will start to roll out with the public releases of iOS 17.4 , iPadOS 17.4 , macOS 14.4 , and watchOS 10.4 , and is already in thedeveloper and public genus Beta releases .