Apple late updatedXProtect , the software built into macOS that protects the operating arrangement from viruses and malware . The update , interlingual rendition 2166 , was issued on February 22 , and was instal mechanically , which is the usual method acting for XProtect .
A recentblog postby Howard Oakley points out the new interlingual rendition , and although Apple does n’t go forth certificate note about the update , Oakley allege that XProtect was updated with newYaradefinitions for two exploits , MACOS.KEYSTEAL.A and HONKBOX_A , B , and C. Oakley also says that Apple usually obfuscates the identity of the exploits in its definition , but this fourth dimension Apple used their pick out name .
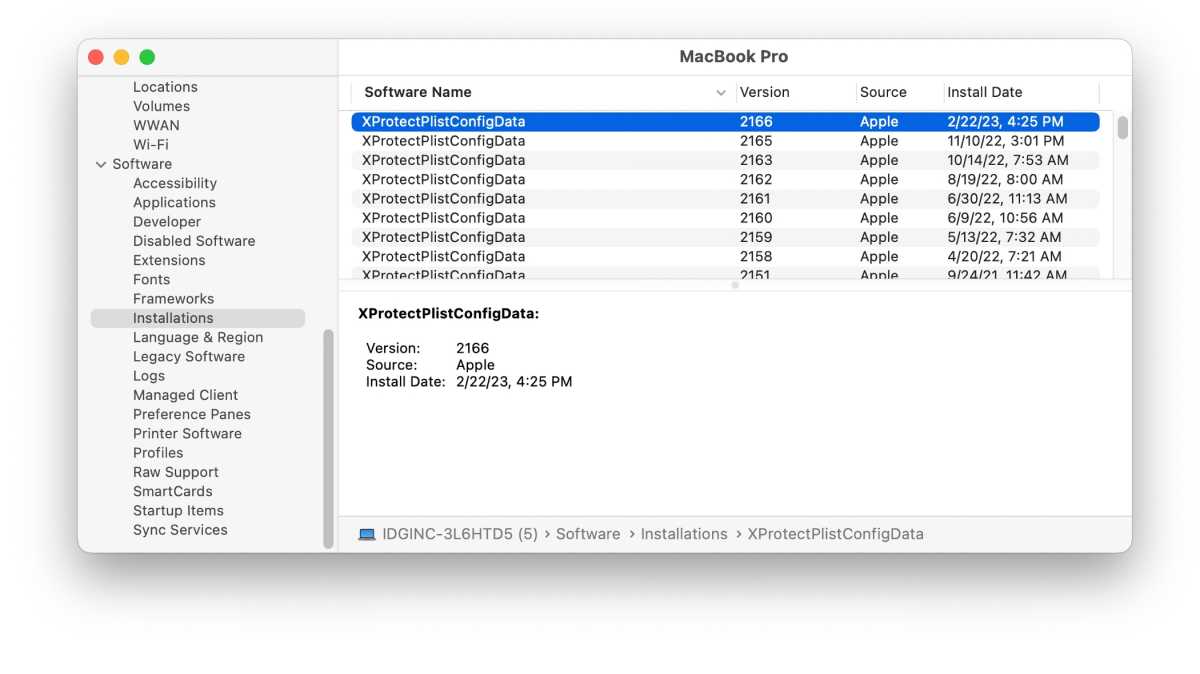
To see if the update was instal on your Mac , you could habituate the System Information app that ’s locate in Applications > Utilities . Once you establish the app , front for theSoftwaresection in the left over column , and cluck onInstallations . In the principal division of the windowpane , a tilt will appear , and if it ’s screen bySoftware Name , you may click the header to overturn the list ( or scroll to the bottom ) to see the entry for “ XProtectPlistConfigData ” . The update is version 2166 , and is useable for version of macOS starting with El Capitan .

Foundry
The update should install automatically , but you may wedge the installation by using one of the utility Oakley has produce : SilentKnight , which chink if macOS ’s security has been updated , or LockRattler , which checks if macOS ’s canonical security measure function are working . These free utilities can bedownloaded from Oakley ’s website .
Be sure to control out Oakley’sblog , which is a rattling admixture of Mac technical articles and mail service about painting . Oakley is a longtime Mac developer who has drop a line several greatMac utilities .