you could be tracked and have your data intercept from many angles , by legitimate and illegitimate actors alike : governments , criminals , personal enemy , corporate spy , children without moral compass , you name it . Many proficiency rent you write in code and shield your data at rest , on your devices and on removed servers , and in transit .
But there ’s one problem with all the shields you may put up : when you need to practice to apply a internet site , you ’re give yourself aside , whether it ’s from your current locating or via a virtual private electronic web ( VPN ) serve that encrypts your request out to a data point server location from whence it issues . Tracking which place you jaw or observe VPN end points can unveil a lot , even if the contents of sitting ca n’t be watch . And websites and VPNs can beblocked , as militant and average citizens in many countries have discover .
There ’s a agency around this . Anonymous browsing hope some of the benefit of dodge tracking from trafficker , crook , and spies , while also give you access to information you need . It does n’t work for every website and comes with a long list of provisos . However , it ’s extremely easy to place up and habituate , and even the workarounds in countries that undertake to obstruct anon. browsing are n’t yet onerous .
( This column is part of an on-going series on ways to protect yourself as if you suddenly find you were a contestant in the country in which you lived . Previous columns manage with passwords , where datum is stored , protecting data in transit , and other subject . )
Use the Tor browser
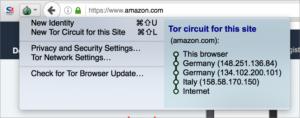
Each Tor school term creates a “ circuit ” through intermediate router , none of which knows the full path .
The Tor Project developsthe Tor internet browser , a multi - platform WWW witness that relies on passing through a series of encrypted tunnels to and between Tor routers that are run by volunteers and organisation around the world . Each sitting , which live about 10 minutes , make a “ circuit ” through a randomly selected set of routers . No router knows about anything except the at once previous and successive connections . Encryption established by the originating internet browser prevents any snoop determine more about the full pathway . It ’s effectively a serial of anonymized VPN tunnels .
The Tor web web browser , which is build as a modified version of the Mozilla Foundation ’s Firefox , enable a number of features by nonremittal , including always - on individual browsing modal value . But it has its own privacy and security configurations , approachable via a green onion plant ikon in the toolbar . ( Tor ’s name once brook for The Onion Router , referring to a proficient definition of onion . )
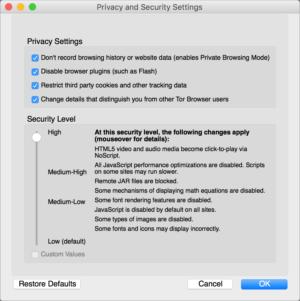
The privacy scope have you clamp down on internet browser characteristics that can be used to track or identify your internet browser uniquely .
In these enhanced setting , the Tor web internet browser ’s typeset several options by default option to make you less easy to dog using well - known techniques that can unambiguously identify a internet browser by install fonts , web internet browser adaptation , platform information , and other data point a statistically substantial percent of the time . you’re able to dislodge up a protective covering skidder high than the nonpayment , reducing the odds of being characterise uniquely , and making it harder for a distant party to have likely footpath for malware .
Tor does n’t solve all job . The undertaking notes that someone discover both a website ’s traffic and your computer could infer that a given seance is related to your exercise ; that ’s a government - scale form of activeness , which could be pinpoint against an individual or could be a country - across-the-board scheme to track as much Tor use as possible . However , that only works dependably for websites that an observer can monitor to match the timing of requests .
And if you sign in or enter identify details at the site you ’re browsing , well , you ’re maybe defeating the use of anonymization , although you still get the general benefit of privacy and a want of tracking .
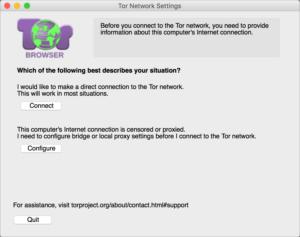
When launch the Tor internet browser for the first prison term , you pick a internet configuration path , which can be changed later .
The web web browser is costless and requires no manual configuration to install and set up . You ’re asked the first time you found the Tor internet browser whether your Internet service provider ( ISP ) blocks connection to the Tor connection or not . If so , you may call for to go through extra hoop , which Tor text file soundly . End point identified by their Internet protocol ( IP ) number exist worldwide and change constantly , and obfuscate protocols allow using these “ bridges ” to go around local blocking .
Because of how iOS lets apps access code meshwork and setting , there ’s no prescribed Tor internet browser for the iPhone and iPad yet . The Tor Project recommends the third - partyOnion web browser , although it ’s not as full feature as desktop versions . In a recent web log Emily Price Post , the project distinguish work underway that might better Tor browse in iOS .
Anonymity is just one tentpole
mention the Tor Project — and I — evade the notion of anonymity , because whenever you ’re using a public resource , like an Internet - reachable website , using an cyberspace - connected gimmick , you ca n’t have anything resembling true or absolute anonymity .
However , as with most well - designed tools design to enhance and protect privacy and security , you ’re coiffe the ginmill much higher , and possibly beyond the reach of , anyone trying to break through to watch over your actions .